8 Power Platform DLP Policy Best Practices

Power Platform DLP Policies determine which data connectors can be used by apps & flows in an environment and which connectors are blocked. They are essential to put in place for every environment. DLP Policies prevent makers from accidentally exposing data to 3rd party services that should not have it. In this article I will share 8 Power Platform DLP Policy best practices and help you build a strategy to prevent data-leakage.
Table of Contents
1. Safeguard The Default Environment With A Restrictive DLP Policy
2. Set A Power Platform DLP Policy For Each New Environment
3. Fine-Tune Connector Endpoints And Actions
4. Use A Shared Power Platform DLP Policy For DEV-TEST-PROD Environments
5. Check Before Changing The DLP Policy For An Existing Environment
6. Create A Blanket Power Platform DLP Policy For The Entire Tenant
7. Update The Governance Error Message With An Admin Contact
8. Do Not Use Power Platform DLP Policy Resource Exemptions
1. Safeguard The Default Environment With A Restrictive DLP Policy
All users with a standard Power Apps/Power Automate license have access to the default environment with the Environment Maker role assigned. Many arrive at the default environment with no prior-training. They cannot be blocked from creating apps or flows so it is important to restrict their capabilities.
Move all non-blockable connectors to the business category.
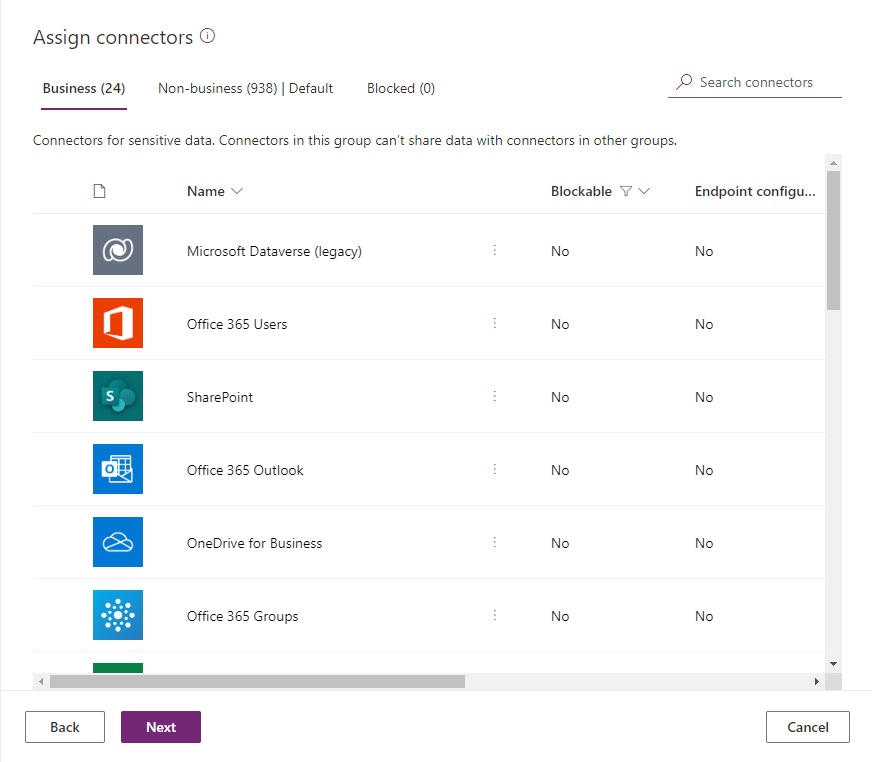
Then move all blockable connectors to the blocked category.
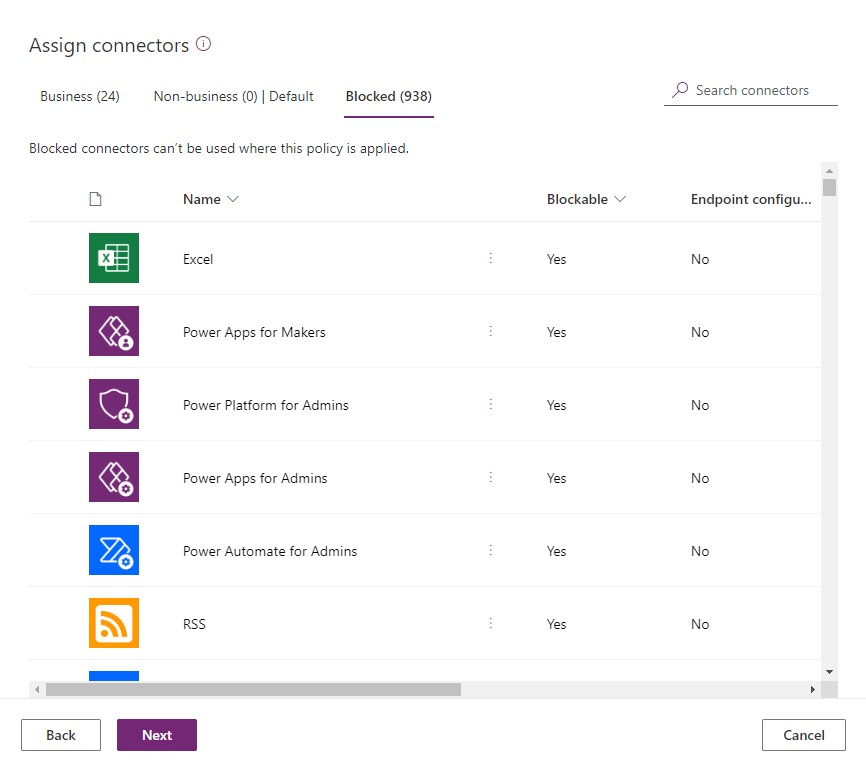
Set the default group for the default environment to blocked. Any new connectors will automatically blocked unless they are non-blockable.
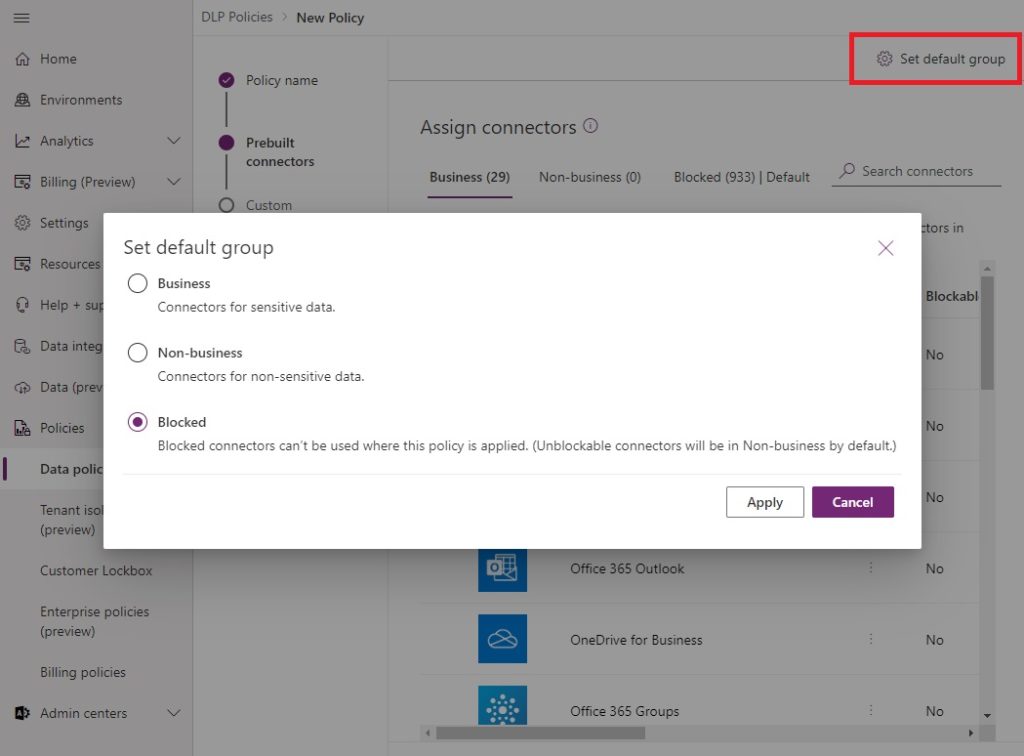
Apply the DLP Policy to only the default environment.
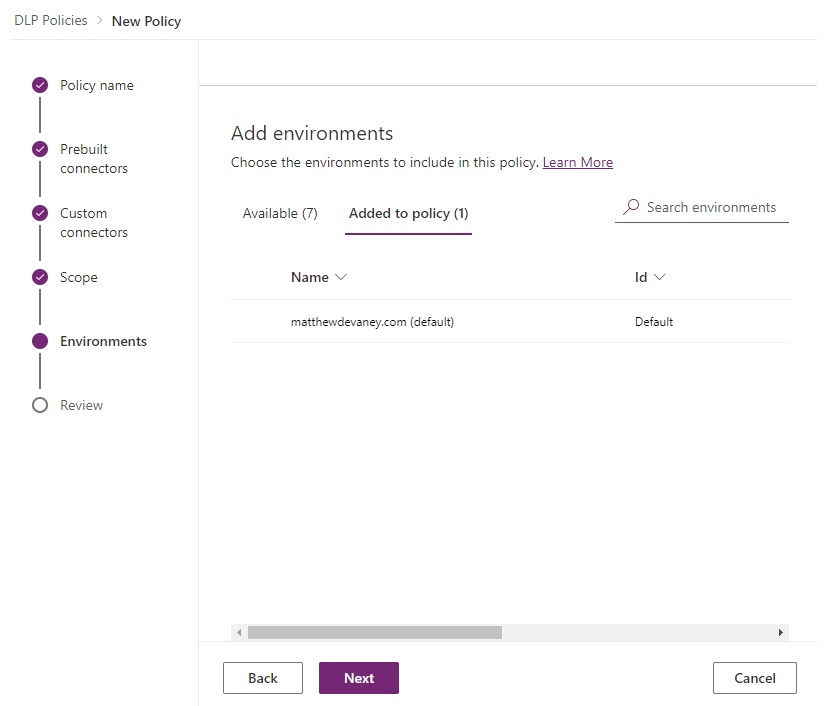
2. Set A Power Platform DLP Policy For Each New Environment
Every environment should have a DLP Policy in place before makers start to use it. When a new environment is requested, start by moving all non-blockable connectors to the business category. Then work with the environment owner to identify any additional connectors that are required (example: Salesforce, SQL Server, etc.) and move them to business as well. Move the remaining connectors to blocked.
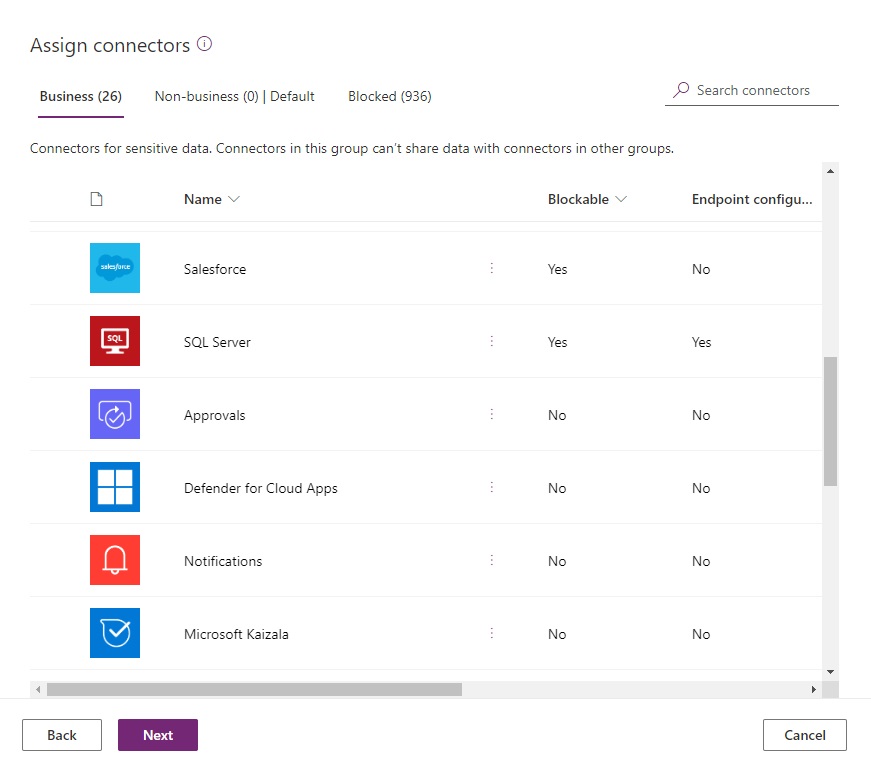
Set the default group for the new environment to blocked.
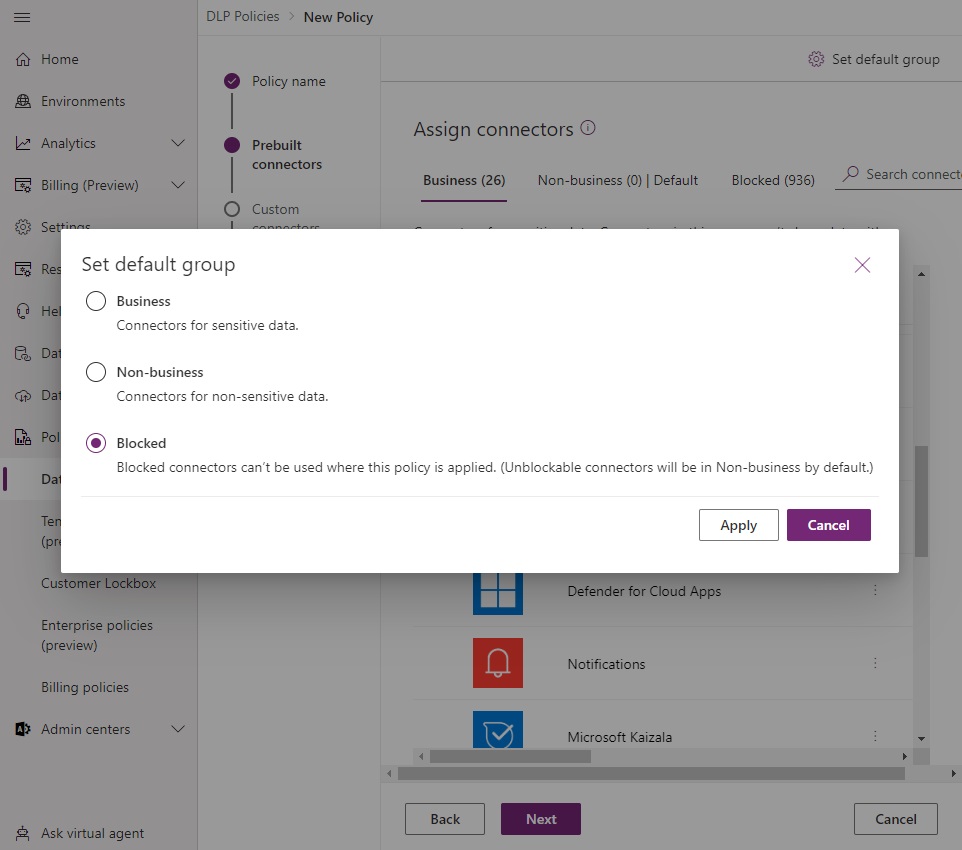
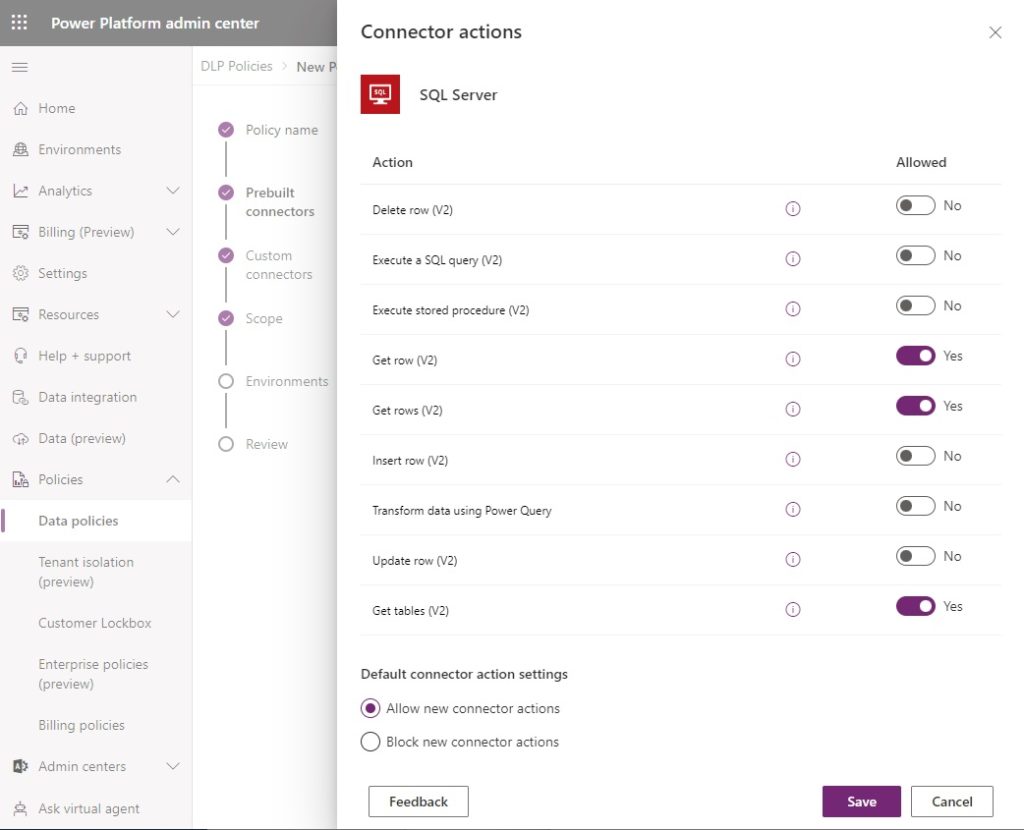
3. Fine-Tune Connector Endpoints And Actions
All blockable connectors can specific actions blocked while allowing others. Others can also allow or deny specific endpoints. Consider limiting usage whenever moving a blockable connector into the business category.
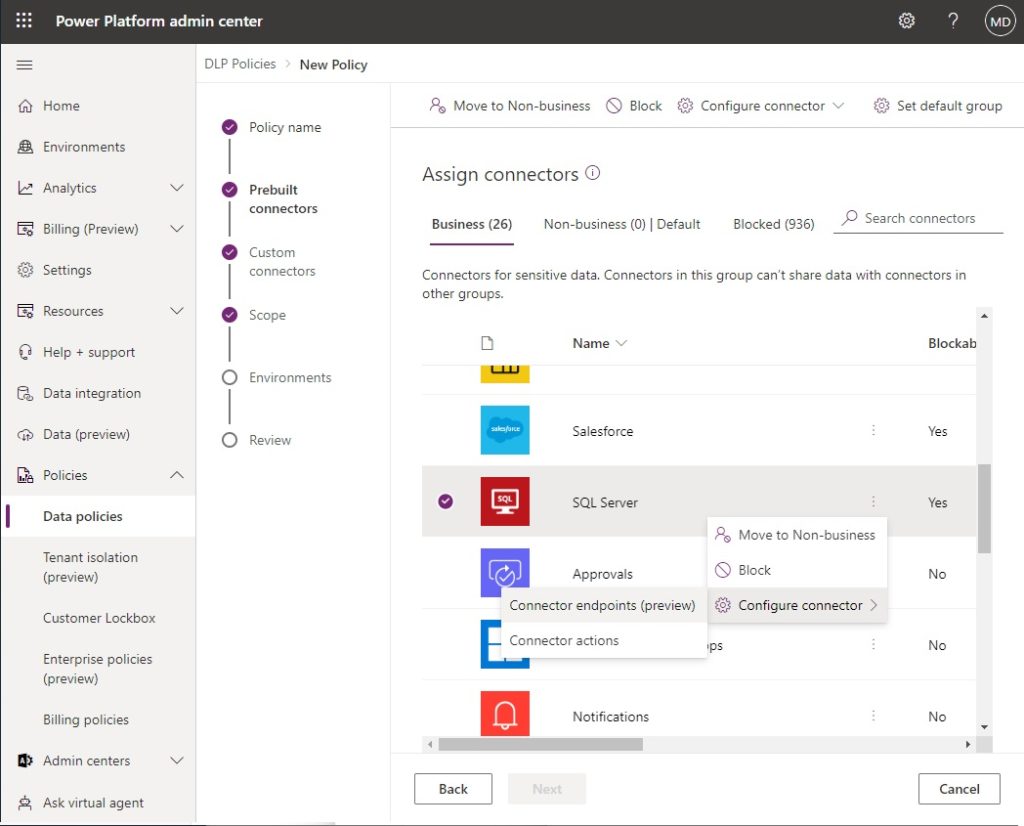
In this example, the SQL Server connector is only allowed to access one endpoint. The idea of what an endpoint is differs for each connector (example: HTTP, Dataverse, Blob Storage, etc.).
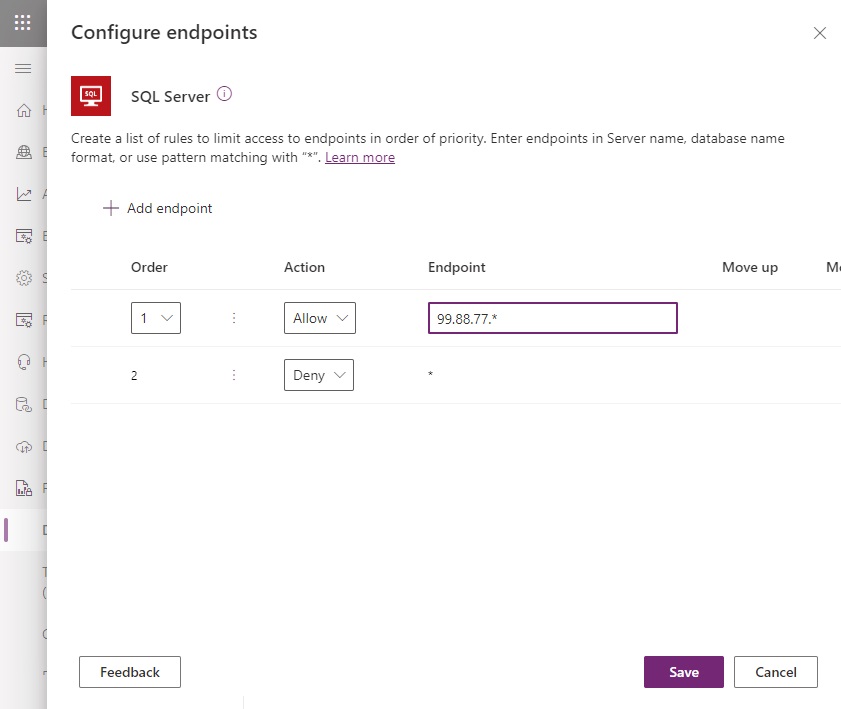
Consider granting read-only access to a datasource using connector actions when users do not have a requirement to insert, update or delete data.
4. Use A Shared Power Platform DLP Policy For DEV-TEST-PROD Environments
New apps and flows should be created in a development environment. Then, they should undergo testing in a test environment and finally be released into a production environment. Include dev, test and prod environments in the same policy to ensure they are always subject to the same conditions.

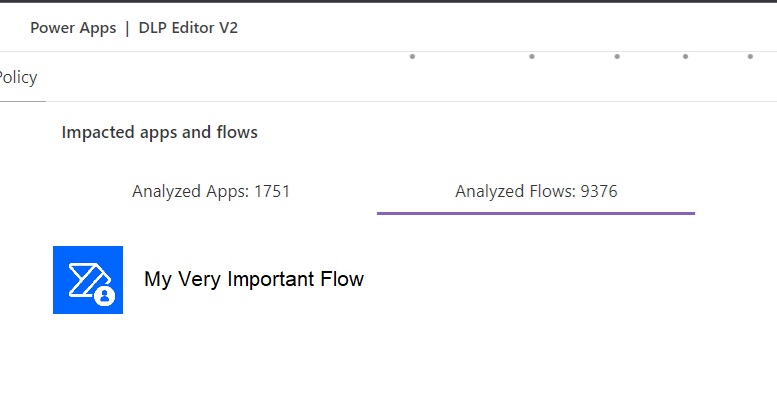
5. Check Before Changing The DLP Policy For An Existing Environment
If a data policy changes after apps & flows have already been developed, it runs the risk of breaking them. The Power Platform Center Of Excellence Starter Kit includes a useful Power Apps app named DLP Editor. Run an impact analysis before switching the data policy to see which specific apps & flows will break. Then inform their creators and find a resolution.
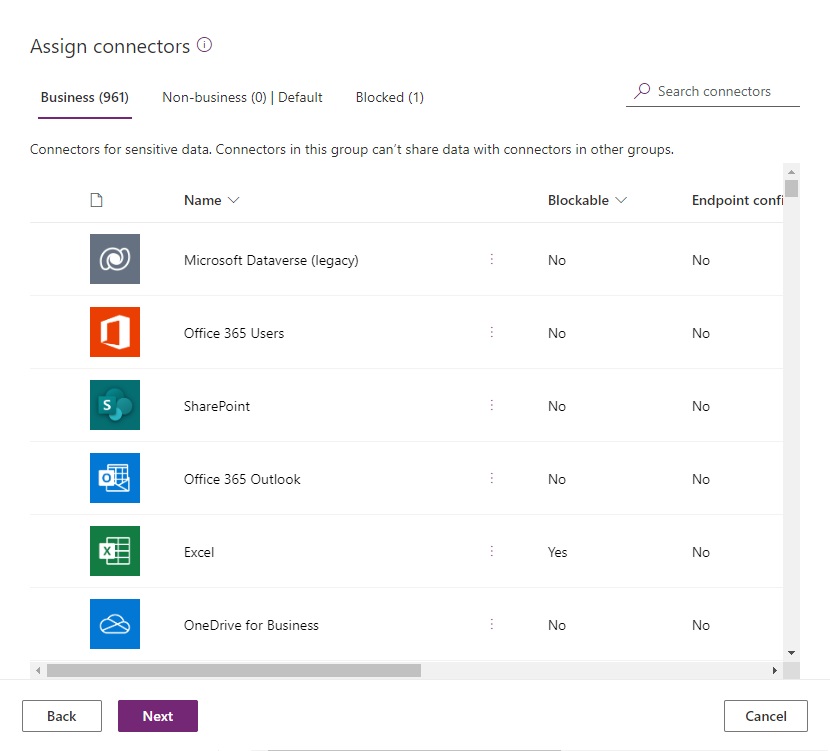
6. Create A Blanket Power Platform DLP Policy For The Entire Tenant
A tenant-wide DLP Policy should be created for the sole purpose of blocking any potentially dangerous connectors in all environments. Do not be overly restrictive here. Blocking too many connectors at the tenant level will harm makers and make administration harder. Only block individual connectors on a case-by-case basis.
The blanket DLP policy will stack on top of the individual environment DLP policies. When one DLP Policy allows a connector and the other DLP Policy blocks a connector, the most restrictive policy wins.
Move all connectors to the business category.
Move individual connectors identified as risky into the blocked category.
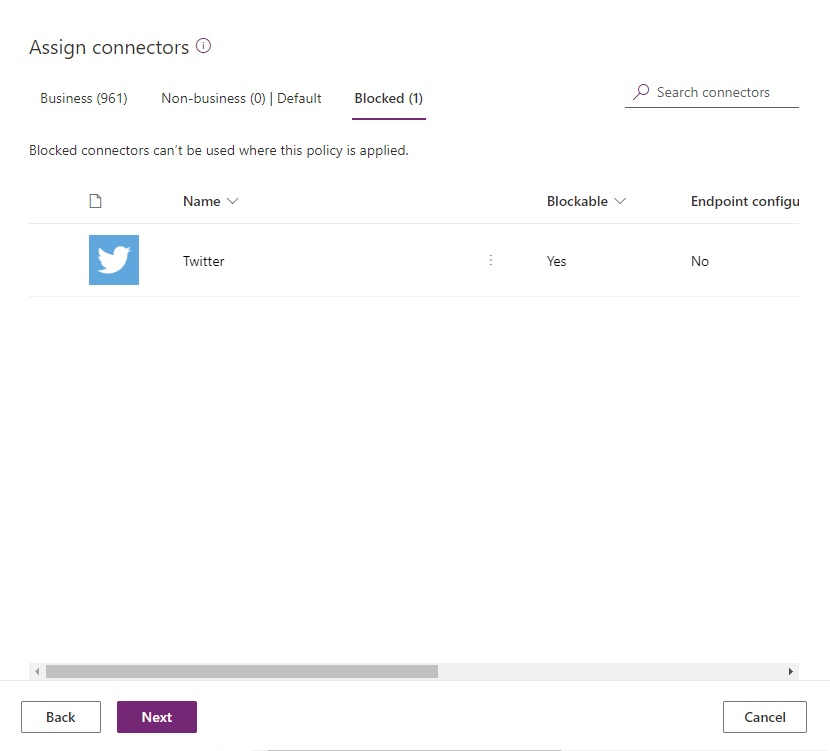
Set the default group to business. Any new connectors added will automatically appear in the business category.
Choose add all environments when defining the scope.
7. Update The Governance Error Message With An Admin Contact
When a maker saves an app or flow that is not DLP Policy compliant they will receive a governance error message. Use PowerShell cmdlets to update the governance message and let makers know who they should contact to resolve the issue.
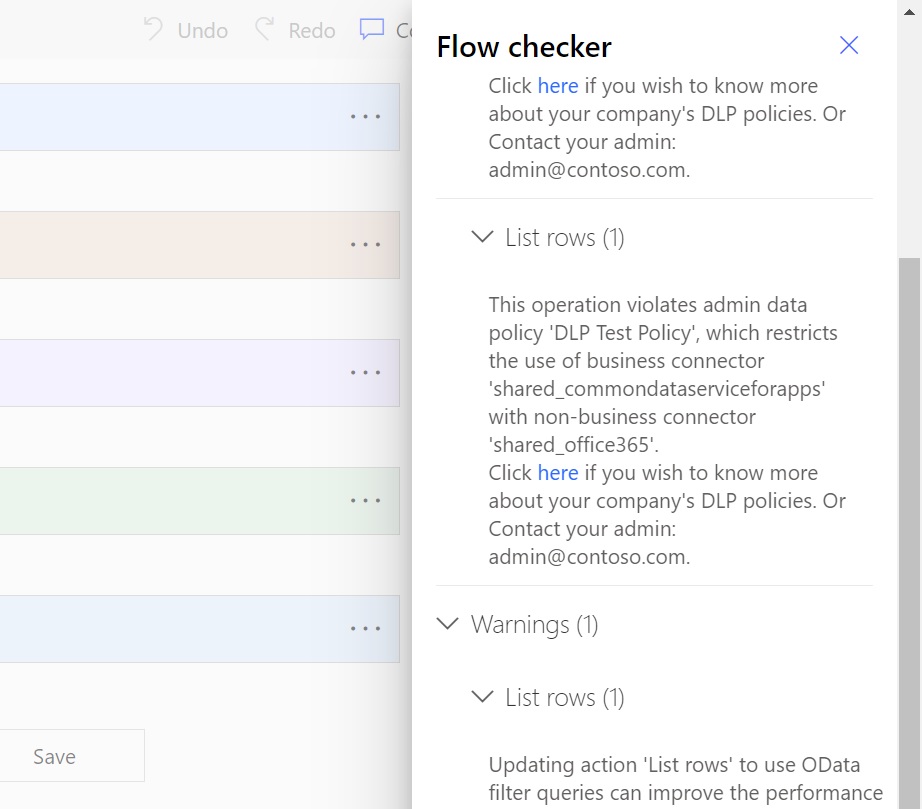
This PowerShell script was used to create the message above. Consider setting up a Microsoft Form and linking it in the governance message to collect requests for DLP Policy changes.
New-PowerAppDlpErrorSettings -TenantId 'TenantId' -ErrorSettings @{
ErrorMessageDetails = @{
enabled = $True
url = "https://contoso.org/governanceMaterial"
}
ContactDetails= @{
enabled = $True
email = "[email protected]"
}
}
8. Do Not Use Power Platform DLP Policy Resource Exemptions
Apps and flow can be exempted from DLP Policies using these PowerShell cmdlets. Do not grant exemptions. If a resource requires a different DLP Policy consider moving it into another environment.
Did You Enjoy This Article? 😺
Subscribe to get new Power Apps articles sent to your inbox each week for FREE
Questions?
If you have any questions or feedback about 8 Power Platform DLP Policy Best Practices please leave a message in the comments section below. You can post using your email address and are not required to create an account to join the discussion.




Great article as always! I never used the exemptions, do they show up anywhere in the admin center or the only way to see that is to enter the Power Shell command to actually see what’s exempted?
Bogdan,
Your are correct. The exemptions are not found in the Admin Center user-interface at this time. The only way to manage/view exceptions is through PowerShell. Microsoft seems to release the PowerShell commands first and the UI updates later. It is meant to get us quicker access to features.
Makes sense to not add exemptions, someone looking at the DLP won’t see them unless they run the command for it so it would get confusing. Good tip!
I love the article! Very useful Thank you very much!
Olena,
You’re welcome. Glad I could help 🙂
I didn’t know it was possible to personalize the violation message.
I think the message come to late for the end user. it appears when you click the save button. very frustrating, especially when you’ve just made a long flow.
Meanwhike, i will look to adjust it like you did
Thank you for this article, very helpful! But how should we handle PP environments for Teams that are automatically created whenever a user creates an app in a Team without any need to request a new environment? Unless I’m getting things wrong here they will only have the tenant wide DLP policy applied which is allowing more access than wanted. Should I as a Power Platform admin continuously monitor for new Teams PP environments and apply a DLP Policy asap on a best effort approach?
Daniel,
Great question! Here’s two ideas:
1) Create a Power Automate flow that applies all new teams environments to a specific DLP.
2) Have a strict global policy and use the exclude to give everything else a way out – then all new environments automatically get the strictest DLP (including teams environments)
Thank you for this article.
Regarding environments with two DLP, if first one covers the entire tenant and the DataVerse connector is in business category . For the second specific DLP, the DataVerse connectors are non-business .
My question is: should I use DataVerse connectors with business connectors or non-business connectors in this Environement ?”
Thanks for the great article! In line with your information regarding changing the Governance Message, is there a way to change the Error Message that is received when attempting to add a blocked connector when adding a new data source? I would like to direct my makers to a Microsoft form where they can request the connector. The message at the moment is not helpful (image below)
Any answer with this?
Great coverage of topics..i am PP admin and System admin as well but i am not able to see where i can create Environment scope policy. is it possible to create an environment dlp as Power Platform admin. I can not find where I can switch from tenant dlp to environment dlp where I can see the custom connectors and not only the option to set the pattern for categorizing custom connectors.