Hide Passwords In Power Automate Flows (and API Keys, Secrets)

The HTTP action in Power Automate often requires a secret password (also known as an API key) to be input. But we don’t want others to see the password when browsing the flow history. By using Azure Key Vault and securing the flow inputs and outputs we can hide this password so no one can view it. In this article I will show you how to hide passwords in Power Automate Flows
Introduction: The Currency Exchange Rate Flow
Employees at a multi-national company use a Power Automate flow to get the current exchange rate between US Dollars (USD) and Japanese Yen (JPY) from the Alpha Vantage API. Access to the API requires a password which must remain hidden from anyone who is browsing the flow history.
What Is Azure Key Vault?
Azure key vault is a service that allows you to securely store passwords, keys, secrets, etc. that are used by other apps and cloud services. We will use it as an online password manager that can interact with Microsoft Flow. When you sign up for an Azure trial you receive a free billing credit which allows you to use Azure Key Vault for free. After the billing credit is fully consumed you can continue to use key vault and it will be added to your monthly Azure bill. It’s extremely cheap – we’re talking pennies on the dollar for most use cases and its well worth it.
Create An Azure Key Vault
We will begin by creating a new Key Vault. Login to Azure and select key vaults from the services category.
Click the create button on the key vaults home screen.
Input a resource group and a key vault name. The resource group helps you track Azure costs on your monthly bill whereas the key vault name identifies the key vault. One finished select the Review + Create button at the bottom of the form.
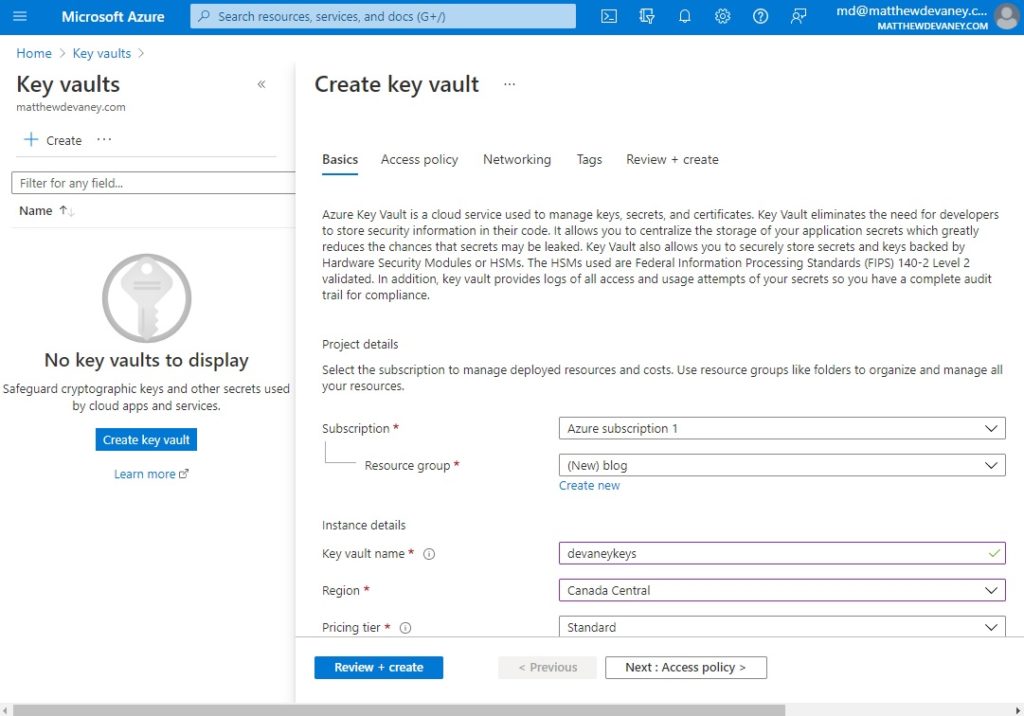
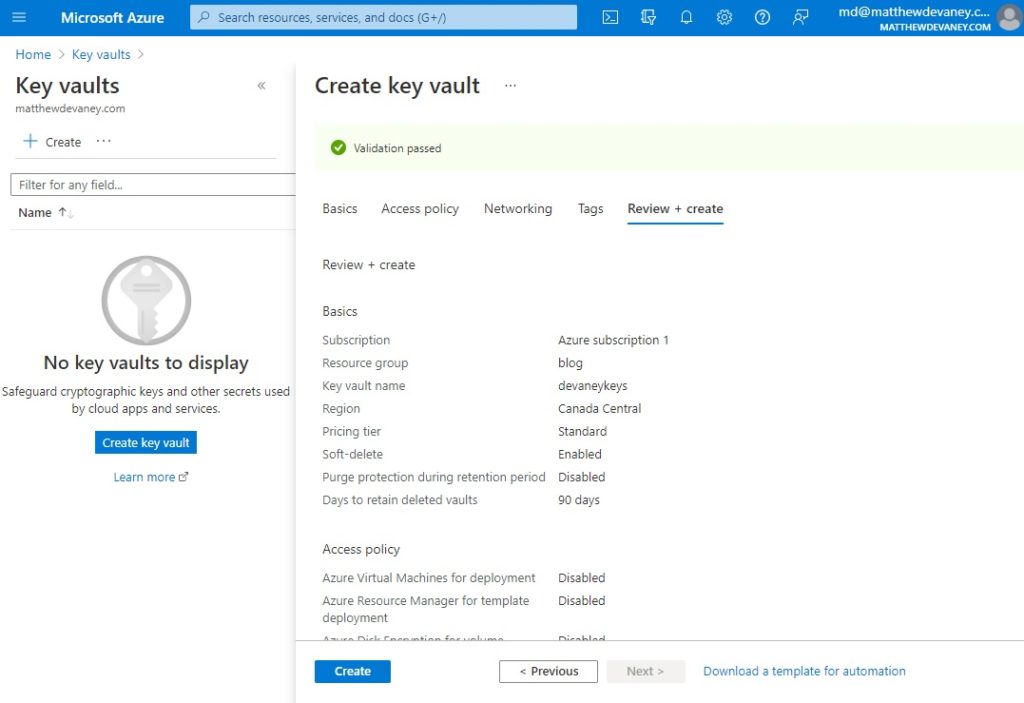
Validation of the key vault will take a few moments to be completed. Once validation is passed click the Create button to end the key vault setup.
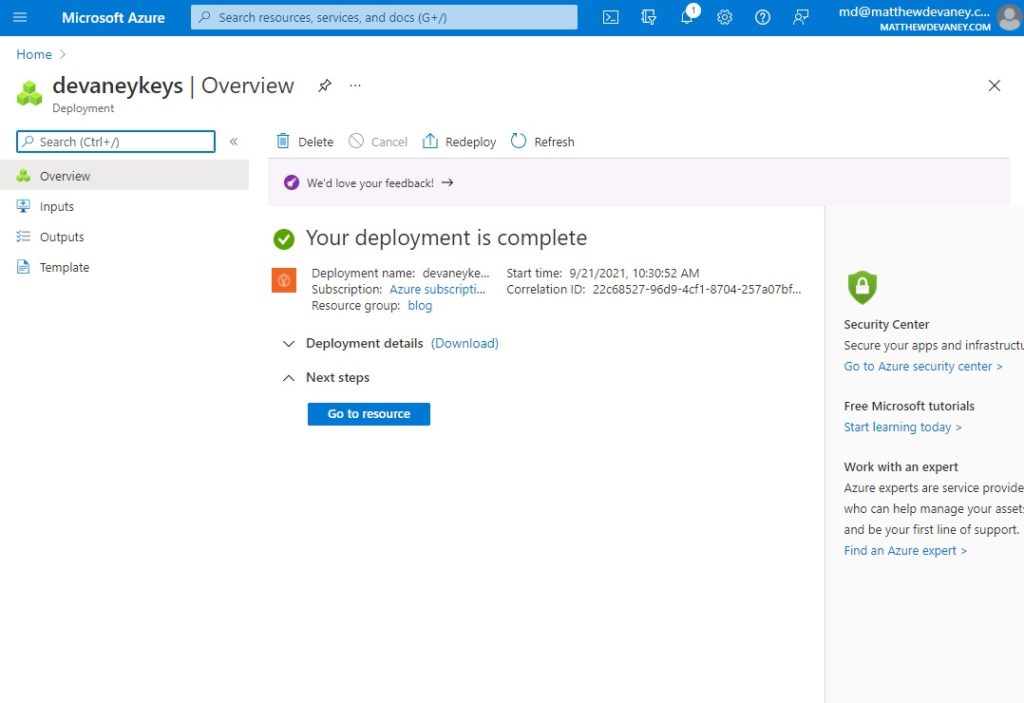
Upon creating the key vault we are taken to a deployment overview screen. Press the Go to resource button to open the key vault (or alternatively search for it in the search bar).
Add A Password To An Azure Key Vault
We want to use Power Automate to get the Alpha Vantage password (i.e. API key) from the Azure Key Vault. The next step is to add a password to the vault. Click on the key vault name to open it.
Use the left-navigation menu to browse to the Secrets page. Generate/Import a new secret.
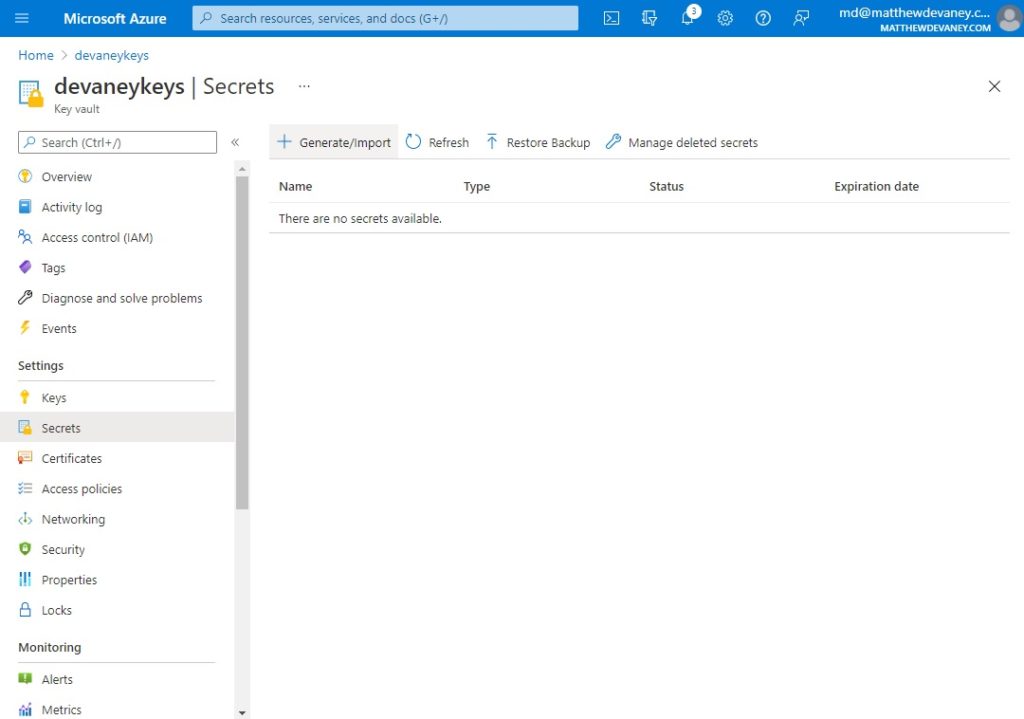
Choose to manually type in a secret name and value. The secret name is the identifier we will see in Microsoft Flow. The value is the password we want to hide. Input value as the 4-letter lowercase word demo and click the create button.
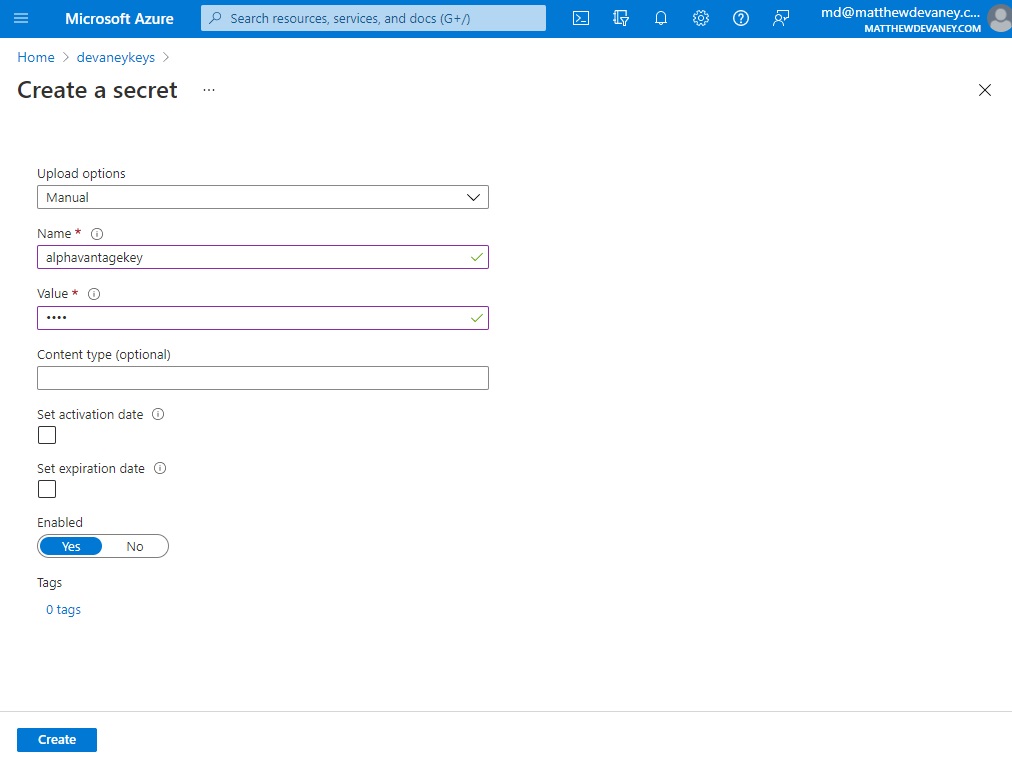
Get A Password From An Azure Key Vault In A Power Automate Flow
Now that we have setup our Azure key vault and creating a secret to store the password its time to create our Power Automate flow. Start a new Instant Flow and add an action called Azure Key Vault – Get Secret. Select the alphavantagekey name from the dropdown.
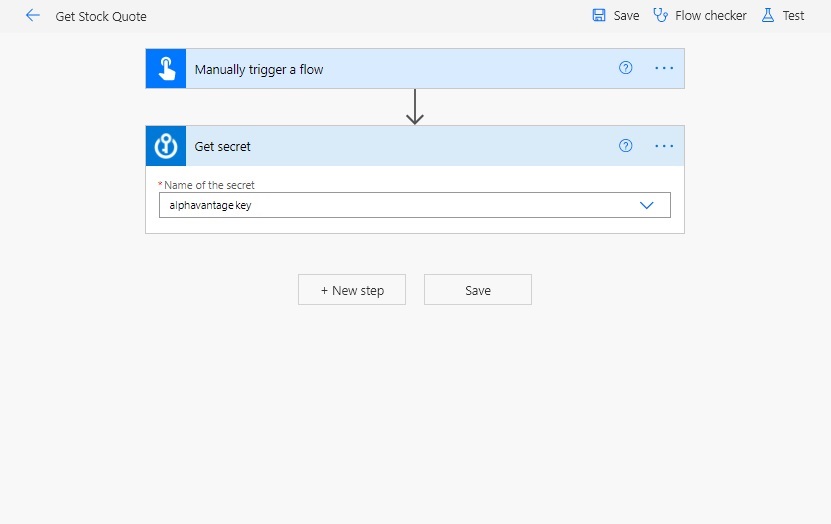
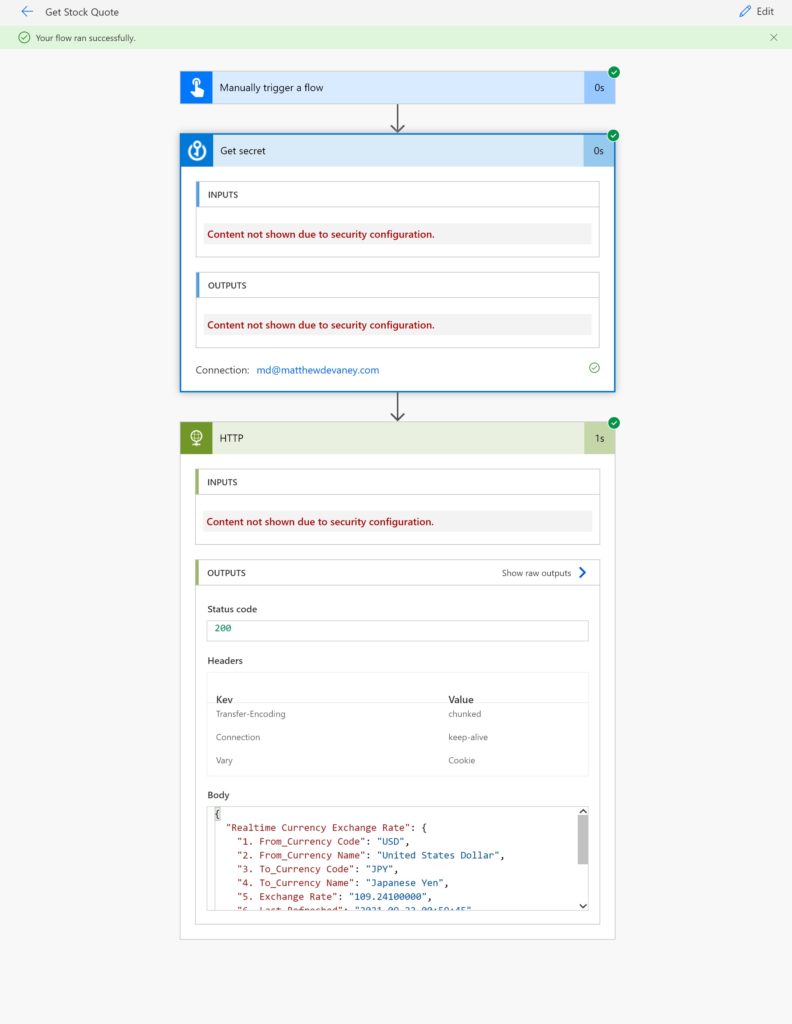
Run the flow to see what happens. The Get secret flow action exposes the secret password. Oops! We need to secure the flow inputs and outputs so users can’t see this information in the flow history.
Hide A Password In Power Automate Flow Inputs and Flow Outputs
To hide the password click on the three dots within the Get secret action and choose Settings.
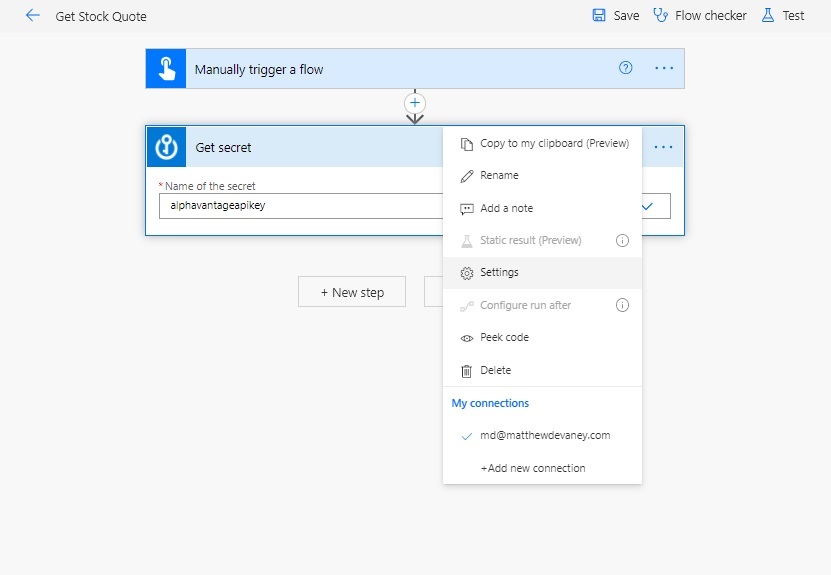
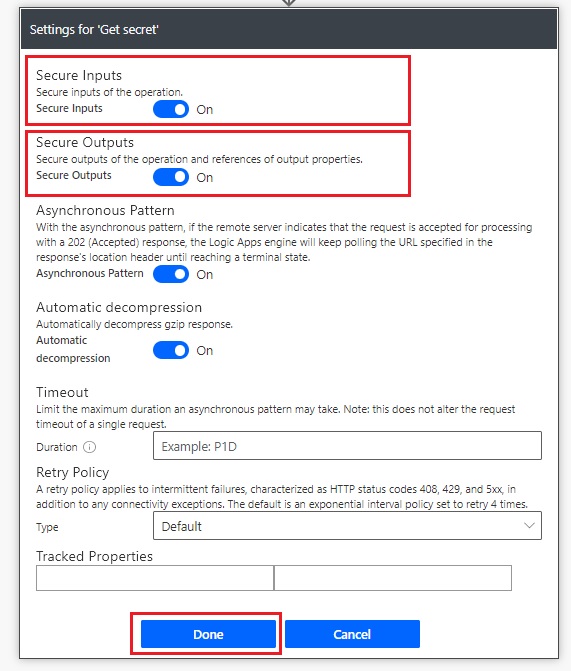
Toggle the Secure Inputs and Secure Outputs options On. Then select the Done button.
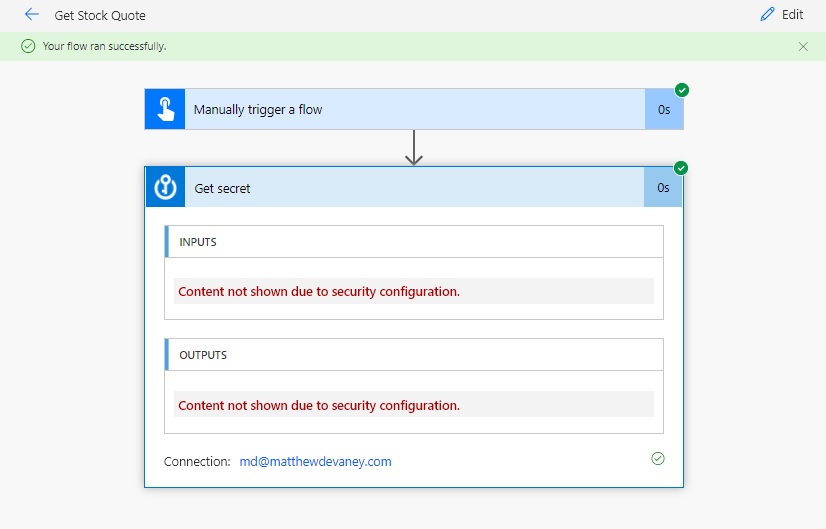
Re-run the flow. Now when we browse the flow history our password is hidden and the message “Content not shown due to security configuration” shows in its place.
Hide The Password For An HTTP Action
Employees at the multi-national company use the Alpha Vantage API to get the current exchange rate between US Dollars and Japanese Yen. Create a new HTTP action in the flow and fill-in the parameters as shown below. Information about how to use the Currency Exchange Rate endpoint of the Alpha Vantage API can be found in its API documentation.
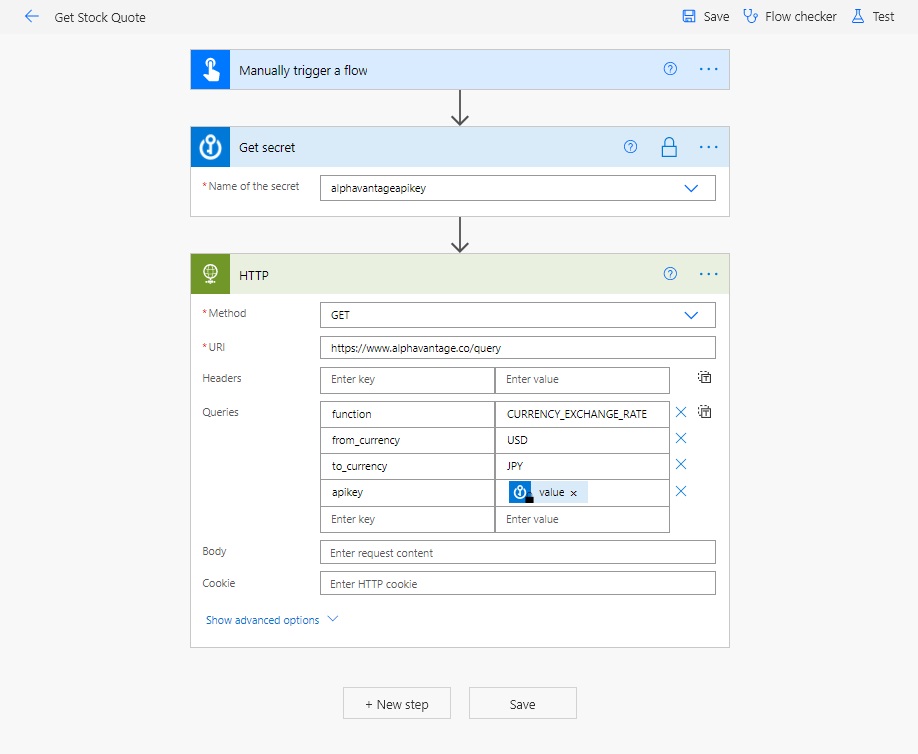
Open the HTTP action settings and toggle Secure Inputs On. We want to see the output of the HTTP action so leave Secure Outputs toggle Off. Click Done at the bottom of the form.
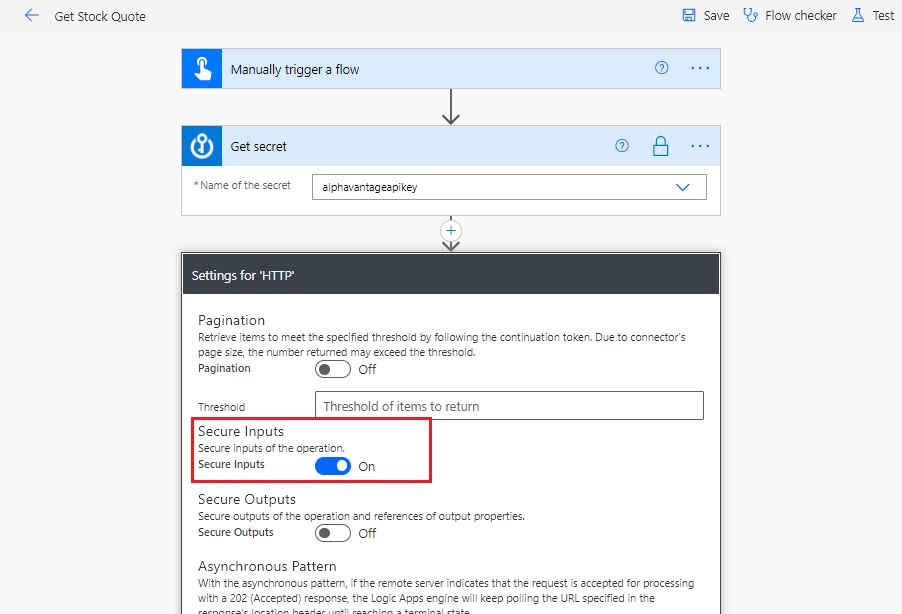
Run the Power Automate flow to give it a test. All of the passwords are successfully hidden and we only see the flow output.
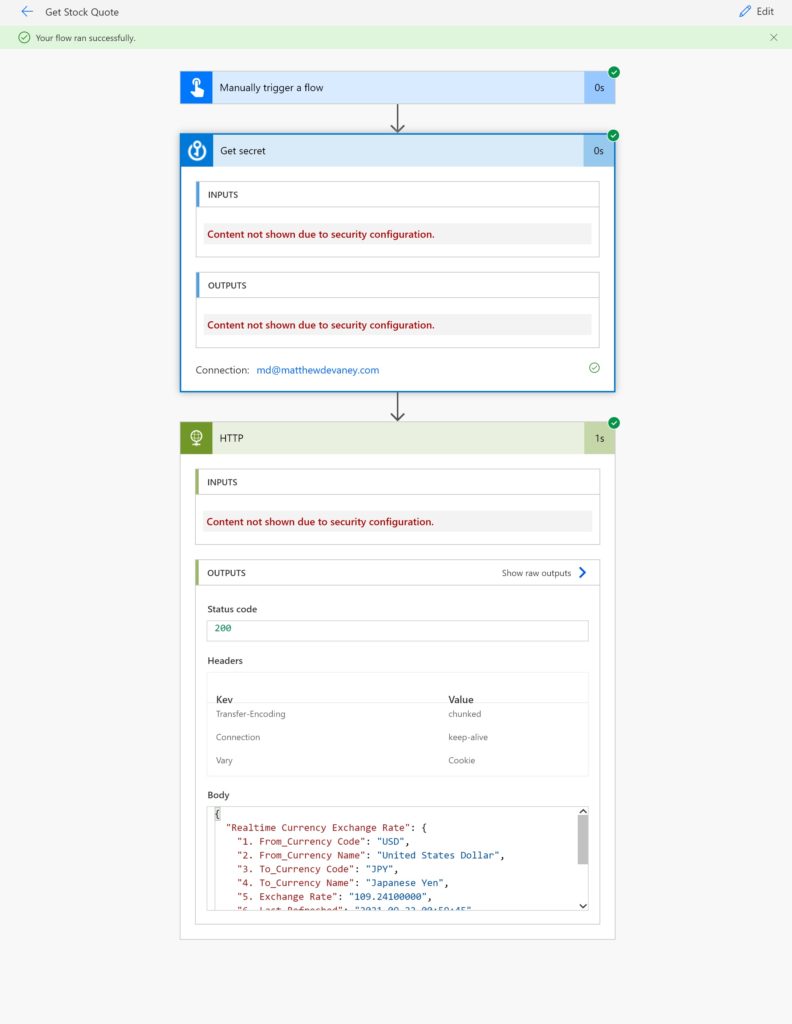
For reference, the resulting JSON object from the flow looks like this and can be used in subsequent flow actions.
{
"Realtime Currency Exchange Rate":{
"1. From_Currency Code":"USD",
"2. From_Currency Name":"United States Dollar",
"3. To_Currency Code":"JPY",
"4. To_Currency Name":"Japanese Yen",
"5. Exchange Rate":"109.42800000",
"6. Last Refreshed":"2021-09-22 01:25:02",
"7. Time Zone":"UTC",
"8. Bid Price":"109.42610000",
"9. Ask Price":"109.43200000"
}
}Code language: JSON / JSON with Comments (json)Did You Enjoy This Article? 😺
Subscribe to get new Copilot Studio articles sent to your inbox each week for FREE
Questions?
If you have any questions or feedback about Hide Passwords In Power Automate Flows (API Keys, Secrets) please leave a message in the comments section below. You can post using your email address and are not required to create an account to join the discussion.





Thanks for the detailed instructions Matthew ! This is very helpful. Are there any alternatives to using the Azure Key Vault for storing the secrets ? Say for eg, maybe a Sharepoint List with restrictive access which could store all the key secrets ?
Nikhil,
I recommend that confidential or highly-sensitive data never be stored in SharePoint. Is there a reason you cannot use Azure Key Vault (which is free)?
Thank you for the post, Matthew, it is really insightful. I just have a couple of questions regarding who has access rights to the Secure Inputs and Secure Outputs toggles on the flow steps. Is it the owner of the flow and anyone else it is shared with or the connection used by the Get Secret and HTTP steps, because it would be counter-productive if wanting to hide the keys from users who have access to the flow, right?
Thanks a milli!
Tinashe,
Great question! It depends how you choose to share the Power Automate flow with another user. If you share the flow with run-only privileges then the end-user cannot turn off secure inputs/outputs. But if you share the show to another user as a co-owner they will be able to disable the security. Think carefully about who needs co-owner privileges before sharing any flow with secure inputs/outputs turned on.
Hi Matthew,
I wasn’t aware of the ability to share the flow with run-only privileges, thanks for that.
Special note: If you’re *testing* before you turn on Secure Inputs/Outputs, and the secrets are in plain text **in your Run History**, and then you share the Flow with someone else, this new person can see the plain text secrets in Run History.
Also: You have to worry about leaky logs showing plain text secrets. Example: If you *have already* authenticated to the Key Vault connector, and turned on Secure Inputs/Outputs, then you run the Flow and it errors out, Power Automate can leak your Key Vault secret in the error message, in plain text.
Hi Matthew, in my organization azure team has the access to key vault and creating secret. so how can I use their created vault and secret in my flow. Cloud team objective is to not share the user name and password to developers. How can this challenge to be solved. Please Help
Varghese,
I don’t know of any way to use a password from Azure Key Vault in a flow and also keep the password secret.
Hello Matthew,
In Graph Explorer I can successfully use the post method to create a new contact.
When I replicate this call in Power Automate using the HTTP action step I can get it to work if I use raw for authentication and then grab the access token from Graph Explorer and put it in as the value for the flow. This works for a day or so until the token expires.
So I went into my developer account where I have global admin privileges and I registered an app in Azure with the correct permissions to create a contact. I actually built two apps in Azure – one with application permission/consent and the other with delegated permissions/consent. I went through the process of capturing the value for the secret and configuring the tenant id and client id and audience in Power Automate. Nothing works. I get some error message related to delegated something or other. (I think it means my Azure app has permission but I as a user don’t and I need a redirect uri to push me to log in every time the flow runs – who knows – bottom line, I can’t get that to work either).
Another rabbit hole I went down was trying to use basic authentication (which is how I ended up here at your post). The message I get from Power Automate is something about my password isn’t formed properly – and when I look in my flow run history I can see that the password inside of the JSON is sanitized.
I’ve tried Co-Pilot and Power Automate community forums – ughh, I’m so close to being able to do what I want to do (which is to get Flow via http using graph to add personalNotes and some other fields that the out of the box create a contact/update a contact in Power Automate can’t do).
Thanks for considering this conundrum of mine. Let’s hope the Jets can do it right tomorrow against the Caps! @geralddahl
Update: two steps resolved the issue. (1) https://laurakokkarinen.com/calling-microsoft-graph-from-microsoft-flow-and-other-daemon-apps-with-delegated-permissions/ has useful configuration steps (2) after part one steps were in place a request I made to my global admin to approve the permissions grant request associated with the Azure app was completed. My flow can now use the http steps from Laura’s blog to get a token which I then use as the value for the second http action which actually deploys the graph step to create a new contact – note that I use raw for authentication in this step.