How To Setup A Power Platform Environment Variable Secret

A Power Platform environment variable secret is a special type of environment variable. It makes a secure connection to Azure Key Vault to retrieve secrets. Only users who are assigned access to the key vault in Azure are able to read the secrets and use them in Power Automate and Power Apps.
Table of Contents
• Introduction: The Open AI Developer Account Secret
• Open An Azure Key Vault In The Azure Portal
• Generate A New Azure Key Vault Secret
• Assign The Azure Key Vault Secrets Role To A User
• Create An Azure Key Vault Access Policy
• Register the Microsoft Power Platform Service Provider
• Add A New Power Platform Environment Variable Secret To A Solution
• Perform An Unbound Action To Retrieve A Secret Value
• Secure Inputs & Outputs To Hide The Secret Value
Introduction: The Open AI Developer Account Secret
An automation development team uses Azure Key Vault to manage their passwords and secrets. A Power Platform environment variable is setup to make the secret value available in Power Apps and Power Automate flows.
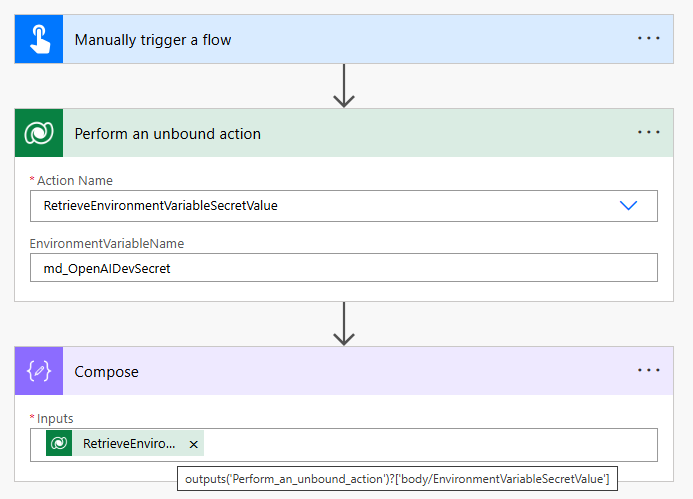
The Power Platform environment variable secret is obtained in a Power Automate flow by using the Retrieve Environment Variable Secret Value unbound action.
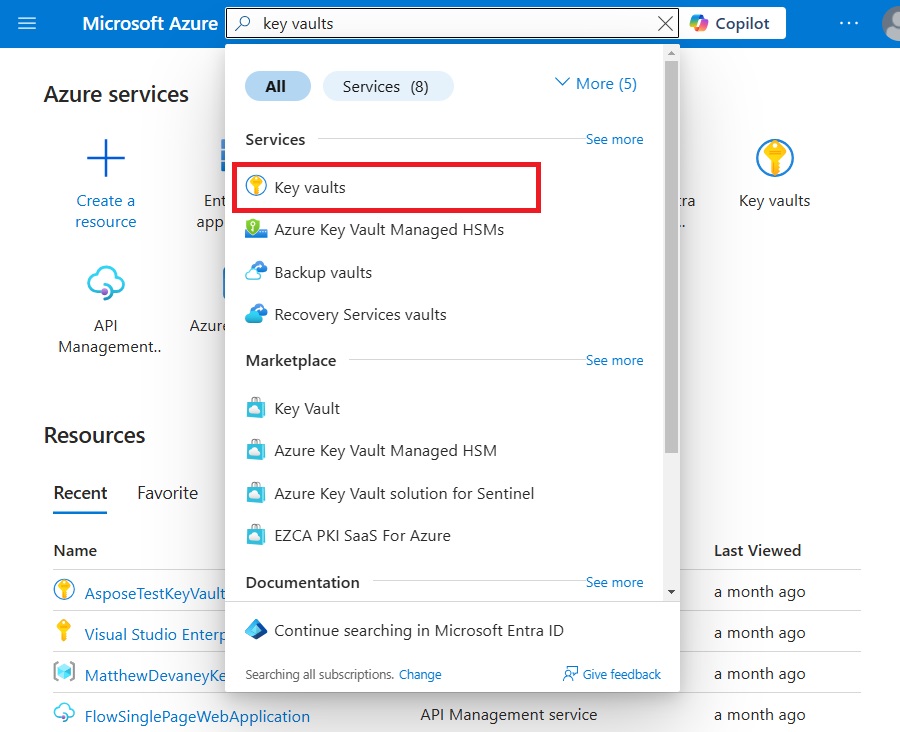
Open An Azure Key Vault In The Azure Portal
Secrets and passwords used in Power Platform can be safely stored in Azure Key Vault. Go to the Azure Portal and open the Key Vaults service.
Open an existing key vault or create a new key vault.
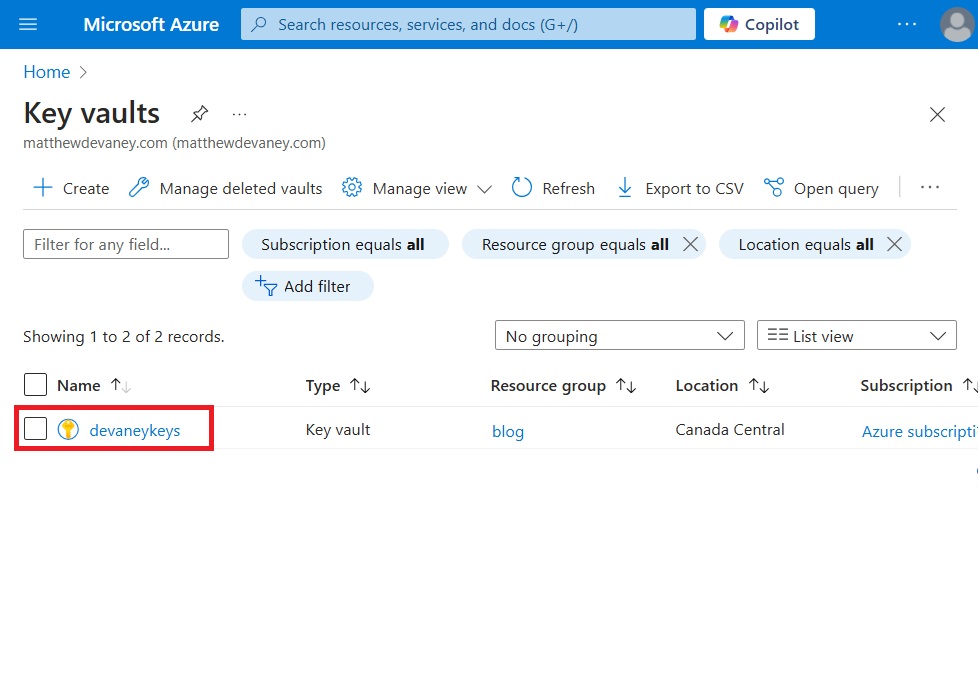
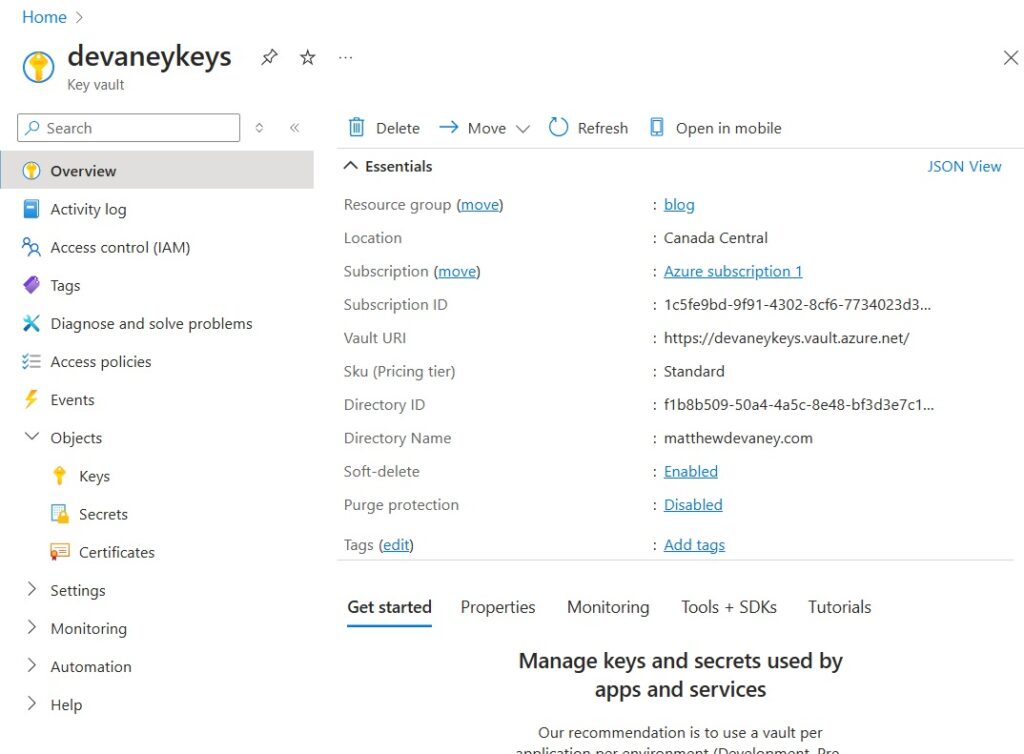
The key vault will open to the Overview page. Here we will find a few pieces of information needed to configure the Power Platform environment variable secret.
- Subscription ID: 1c5fe9bd-9f91….
- Resource Group: blog
- Name: devaneykeys
Generate A New Azure Key Vault Secret
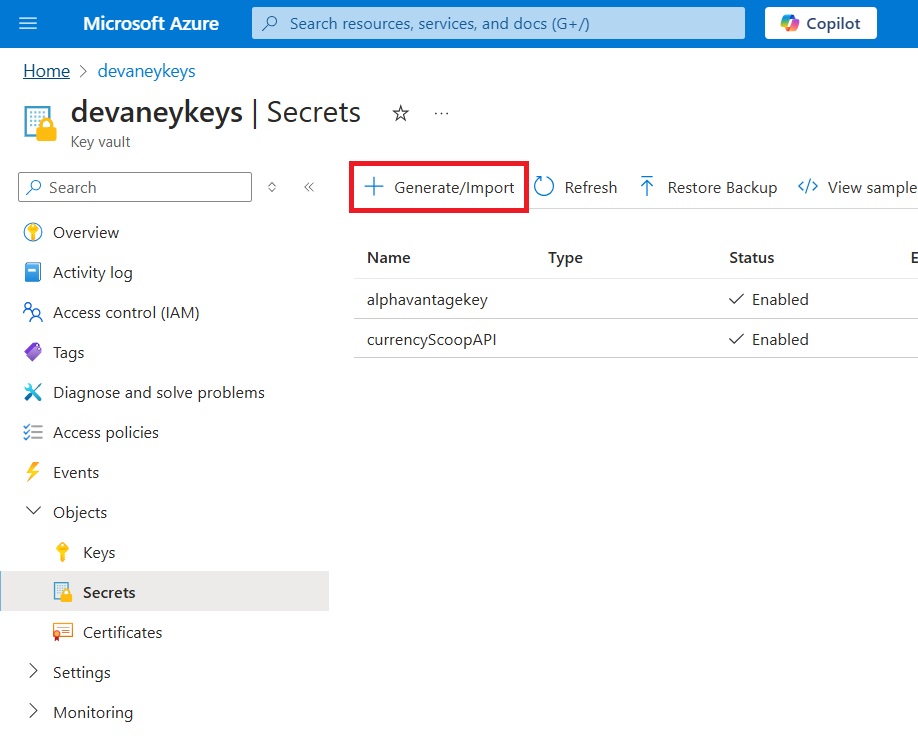
To create a new secret value for use in Power Platform, go to the Secrets menu and select Generate/Import.
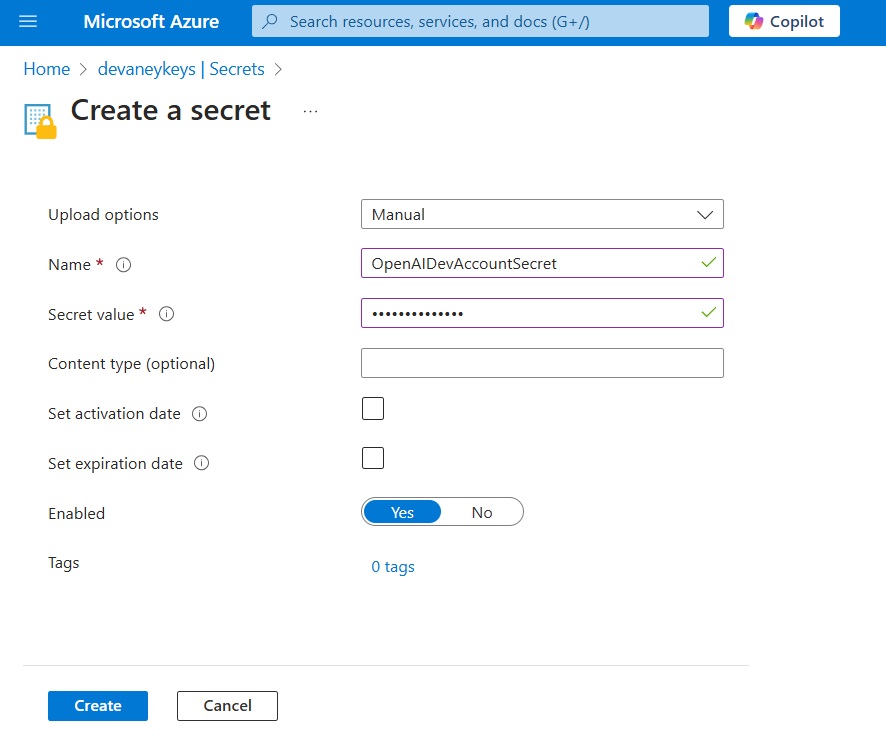
Fill-in the Name, Secret value and optionally set an expiration date. Then press the Create button.
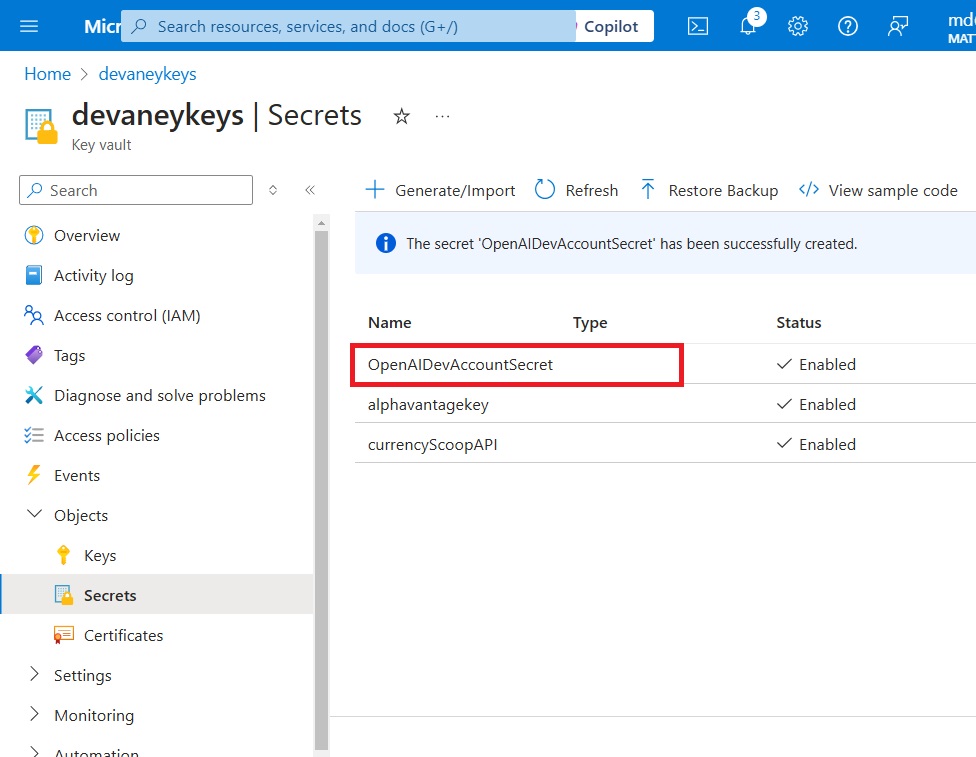
The new secret now appears in the Secrets menu.
Assign The Azure Key Vault Secrets Role To A User
To access the Azure Key Vault the User account who reads the secrets must have the role Key Vault Secrets User. Browse to the Access Control (IAM) menu and press the Add Role Assignment button.
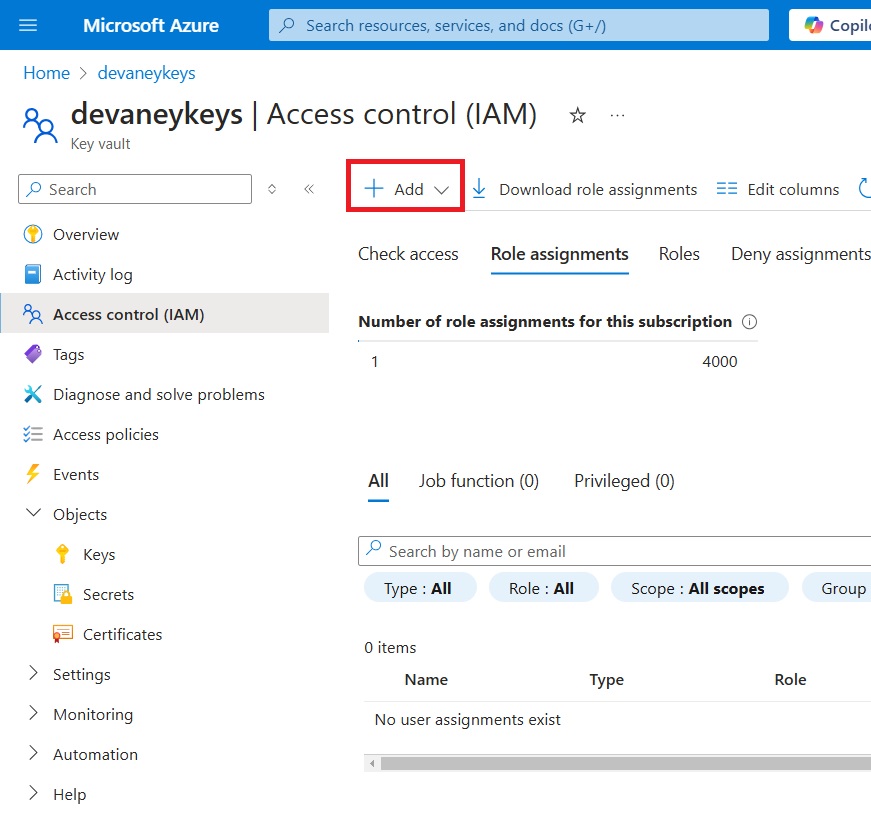
Select the Key Vault Secrets User role.
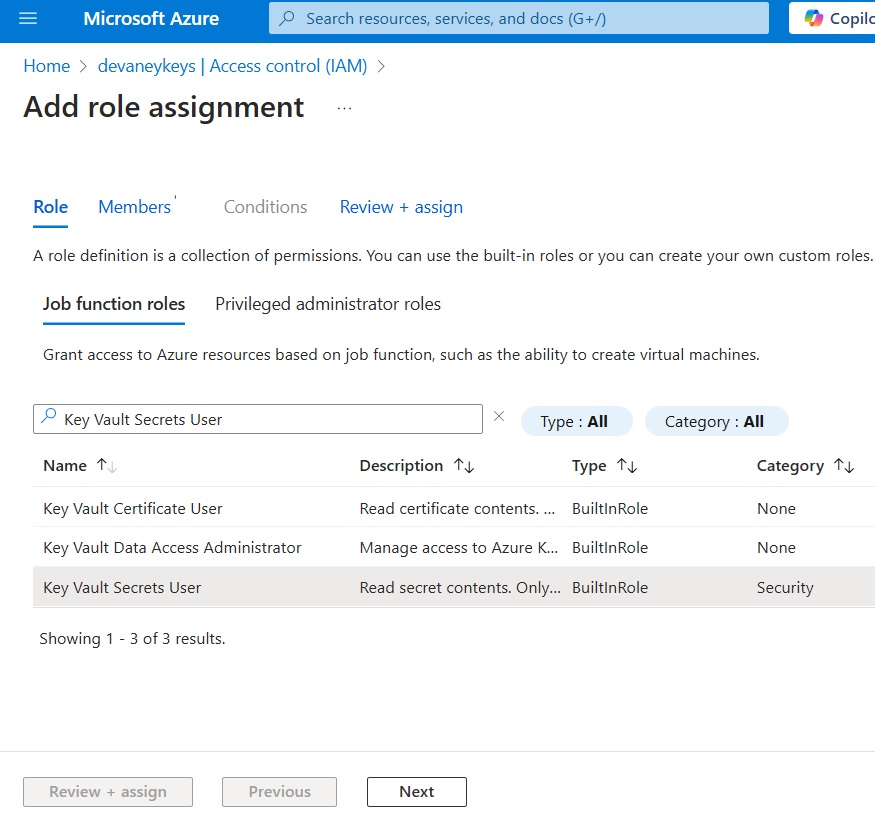
Then assign the User account who will read the Secret in Power Platform. And also assign the application named Dataverse as well.
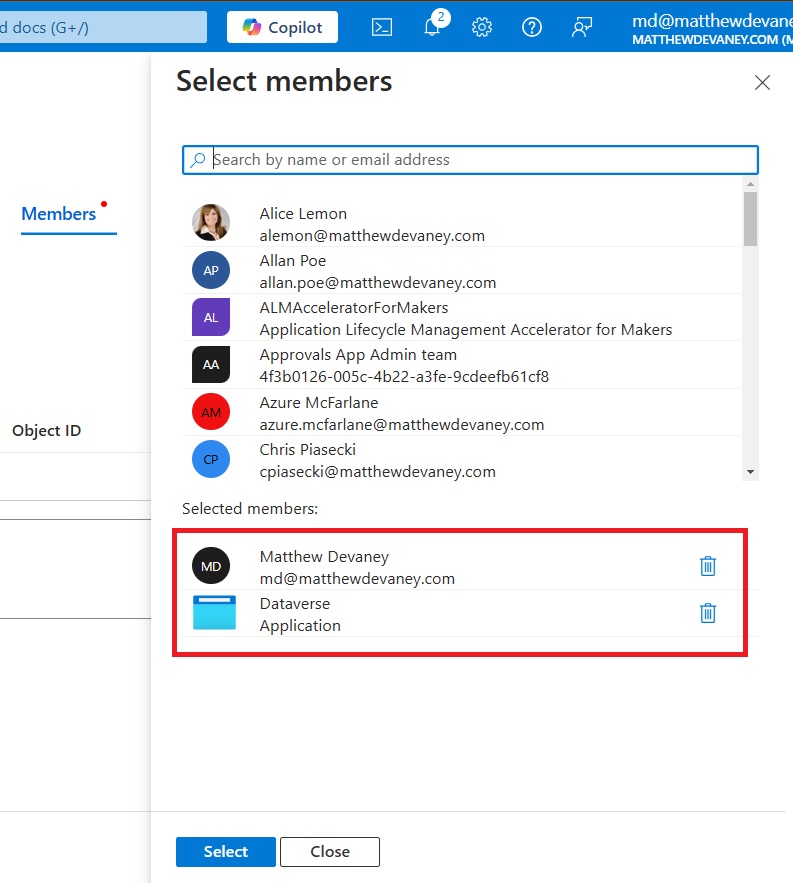
The User account and Dataverse application now show as members of the Key Vault User Secrets role. Press the Review + Assign button.
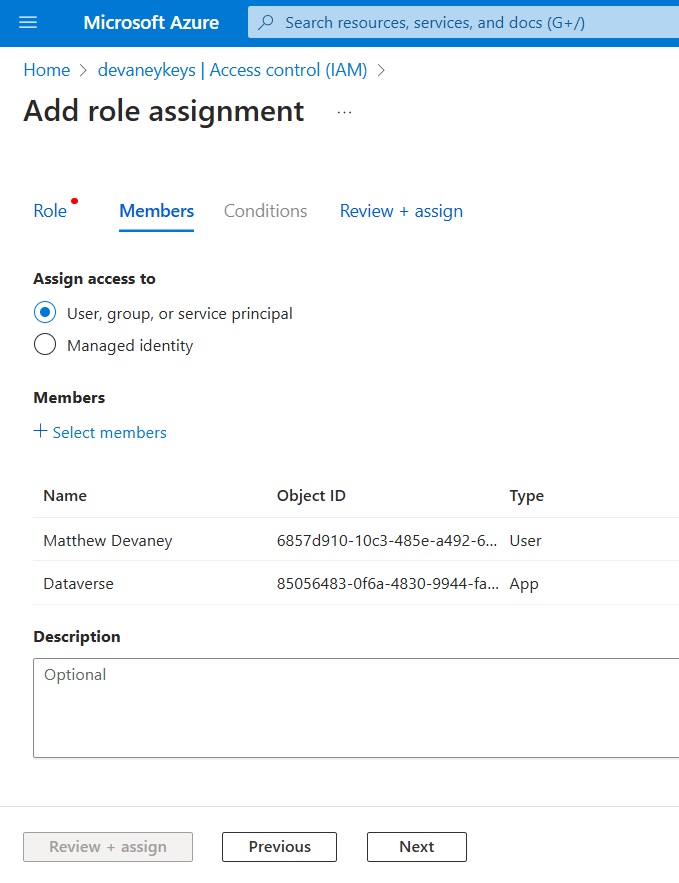
The Access Control (IAM) menu displays the newly assigned users and their roles.
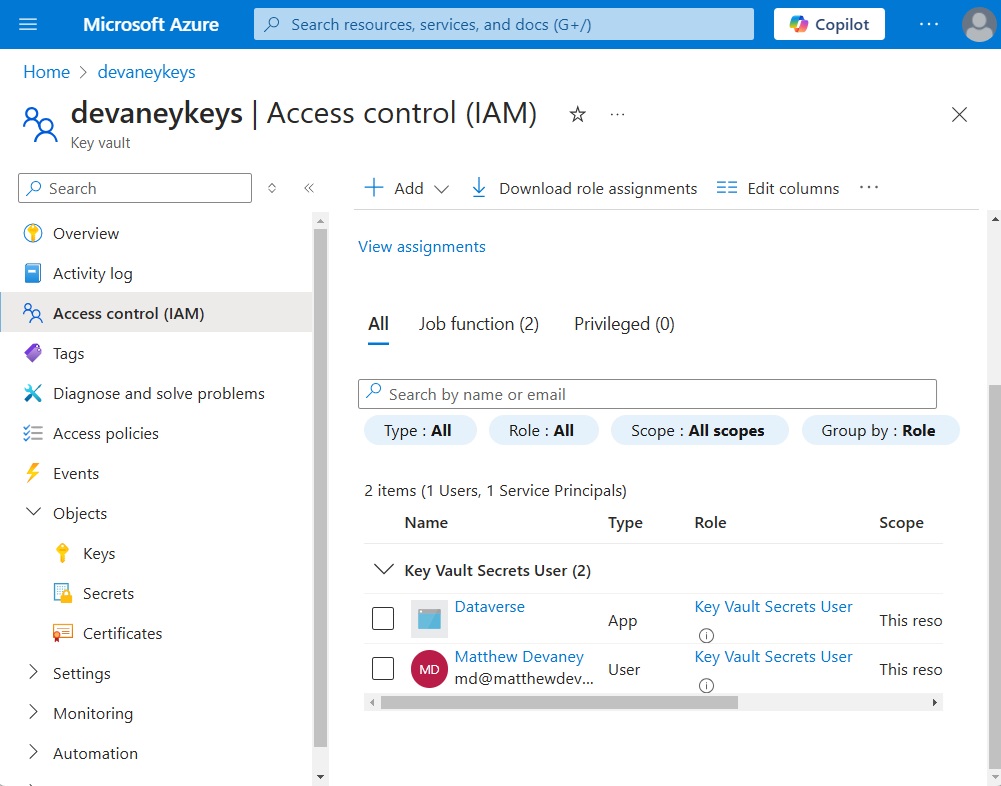
Create An Azure Key Vault Access Policy
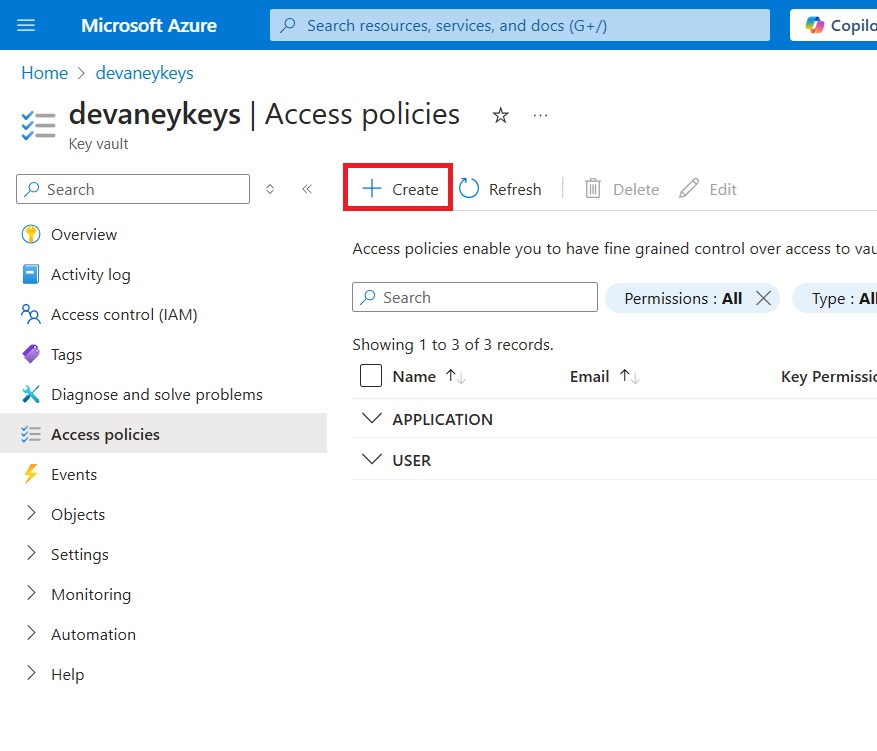
The final setup step in Azure is to assign an access policy to the User account and the Dataverse account. Open the Access Policies menu and select Create.
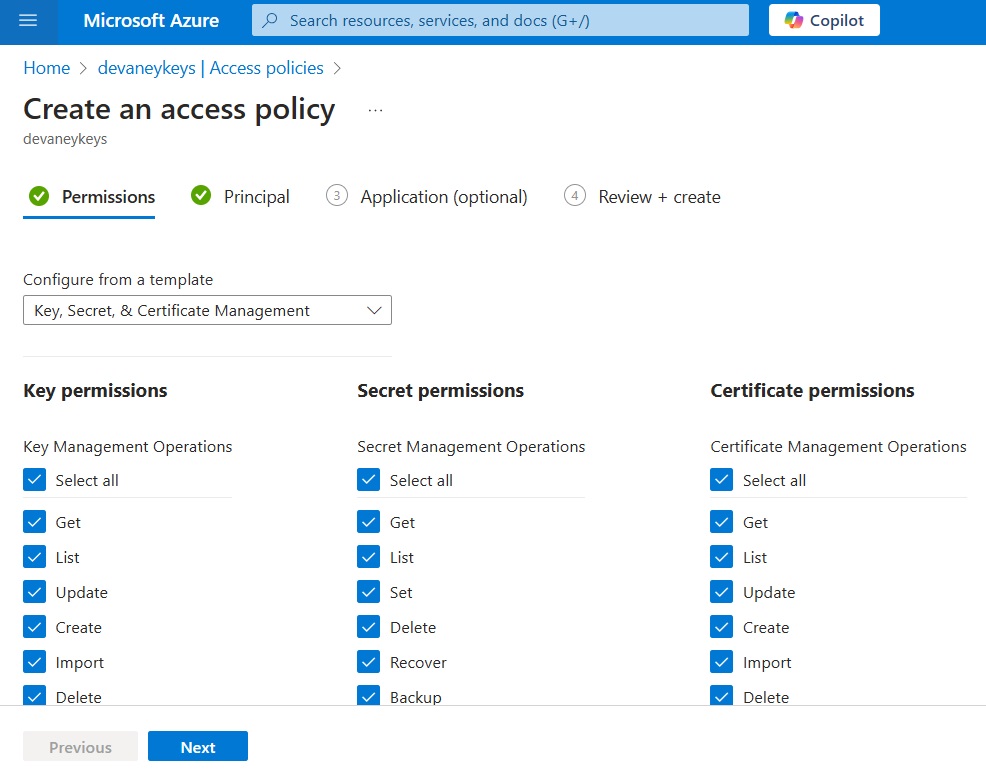
Choose the Key, Secret and Certificate Management template to grant access to all values stored in the key vault.
Select the User account as the principal and complete the Create an access policy process.
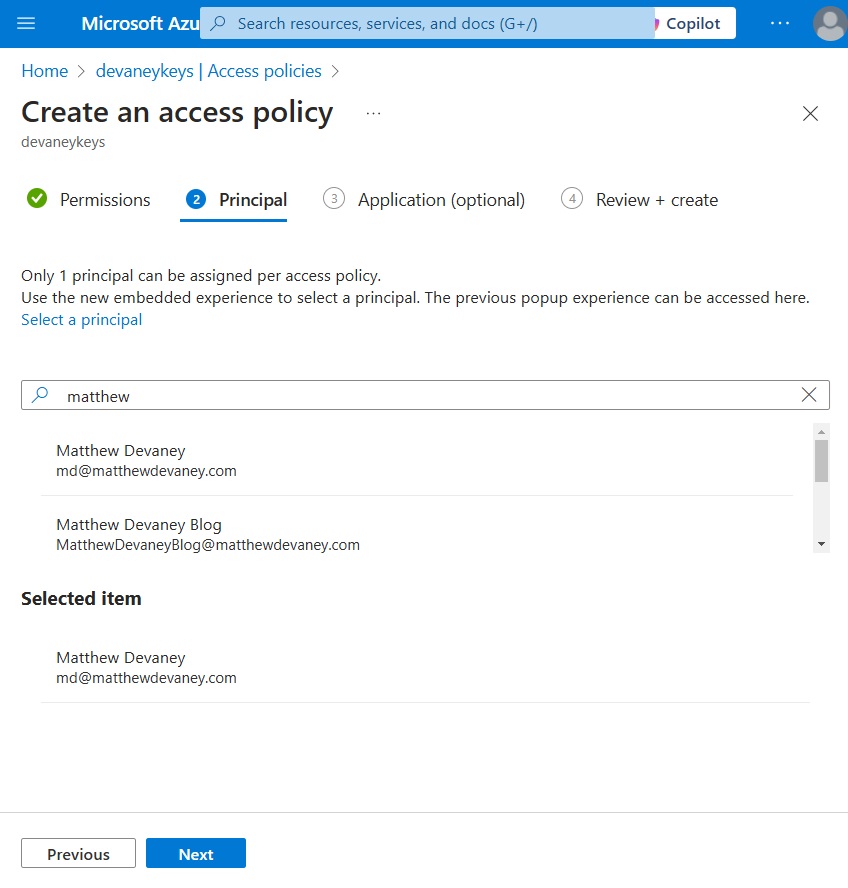
Then create a 2nd access policy with the same Key, Secret and Certificate Management template and choose the Dataverse account as the principal.
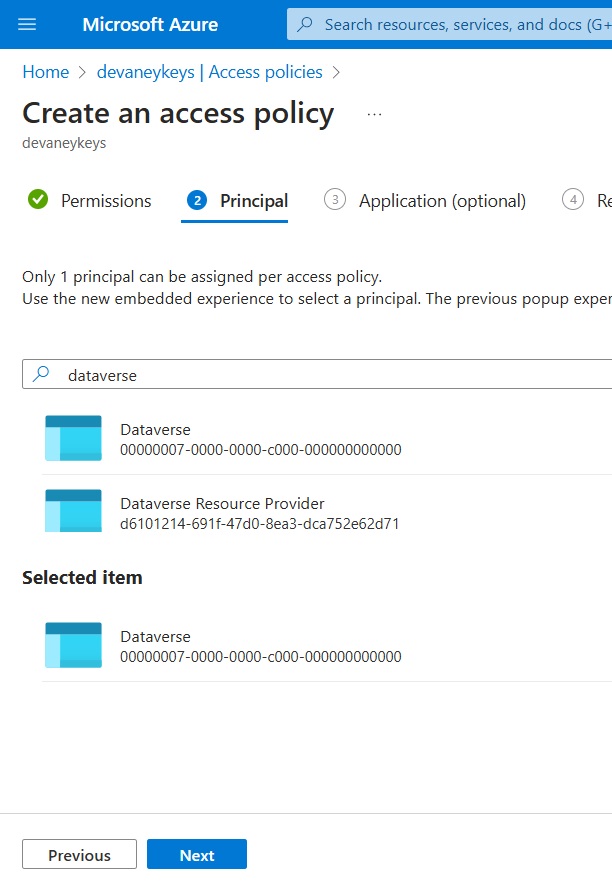
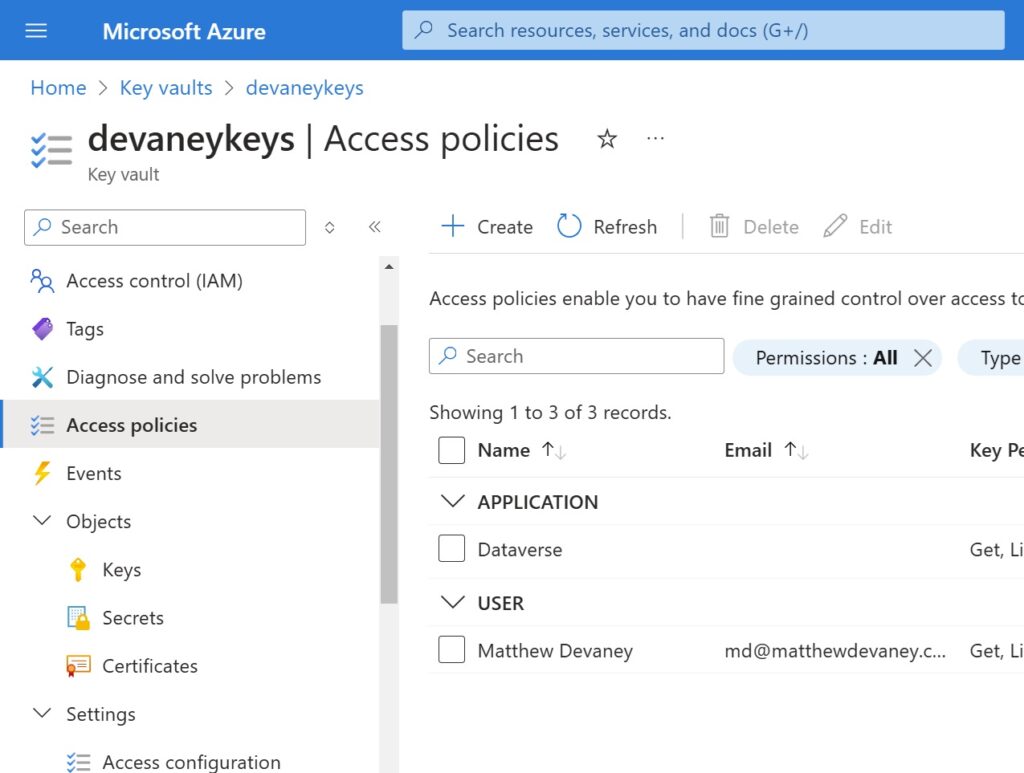
The User account and the Dataverse application now appear in the Access policies menu along with their permissions.
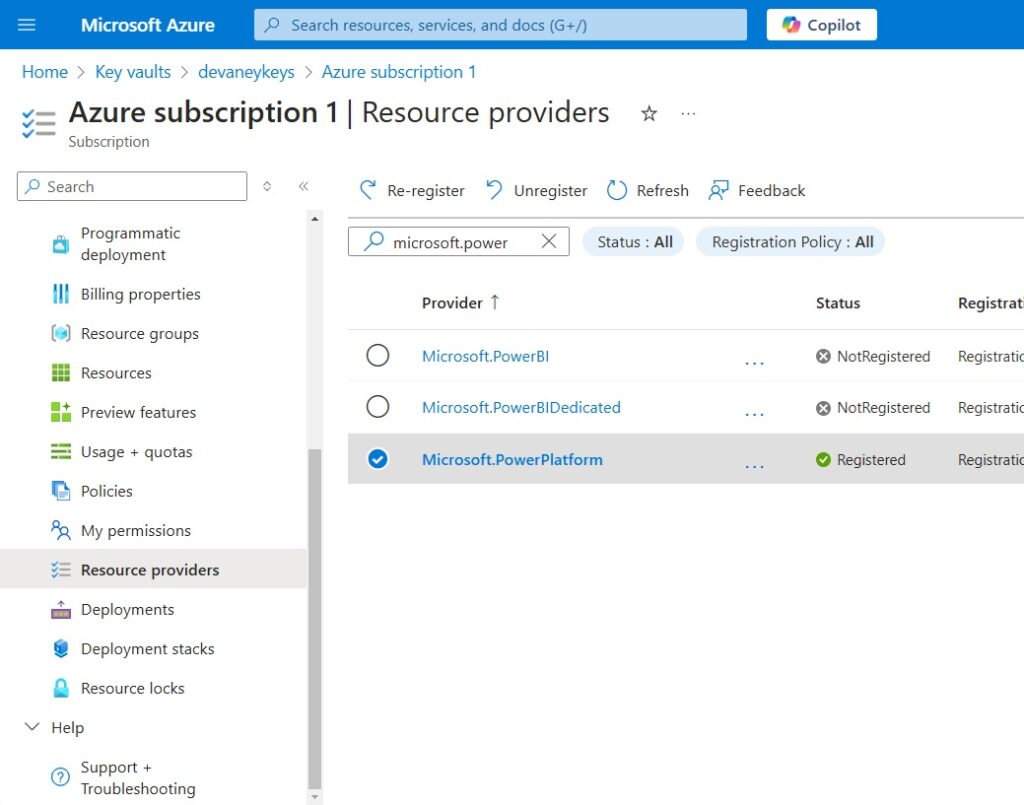
Register the Microsoft Power Platform Service Provider
If the Subscription selected the the Azure Key Vault does not already have Power Platform registered as a service provider, this will be necessary as well. Open the Subscription, go to the Resource Providers menu and check that Microsoft.PowerPlatform is registered.
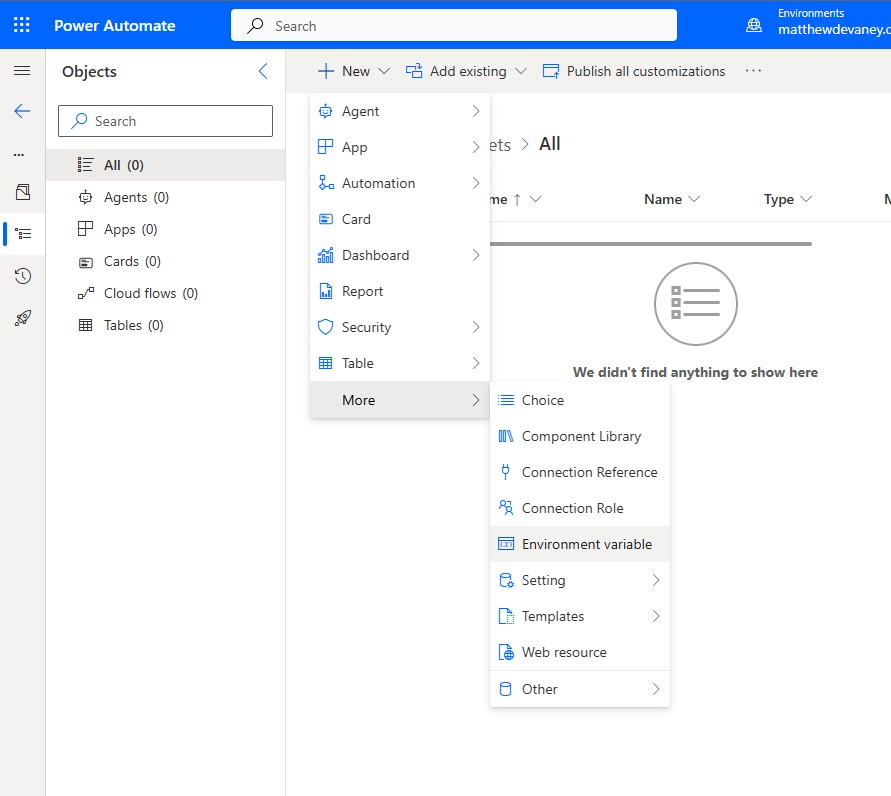
Add A New Power Platform Environment Variable Secret To A Solution
With the Azure Key Vault fully configured, and the new Secret added the next step is to create an Power Platform environment variable secret. Open any solution in Power Automate and add a new Environment Variable.
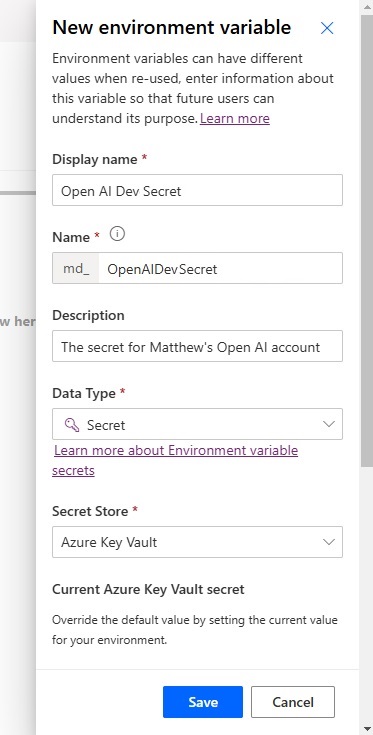
Setup the environment variable with the following details:
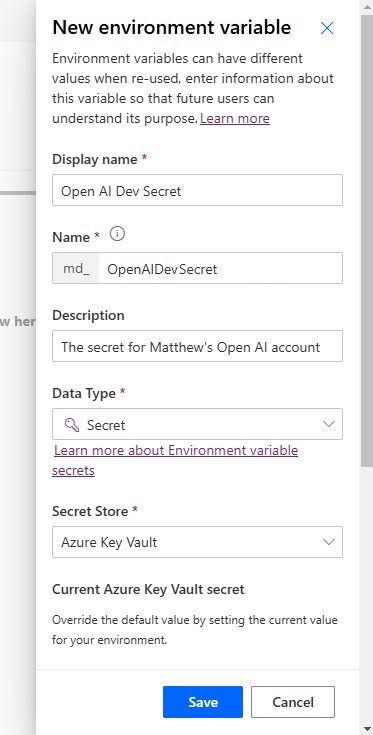
- Display Name: Open AI Dev Secret
- Name: md_OpenAIDevSecret
- Data Type: Secret
- Secret Store: Azure Key Vault
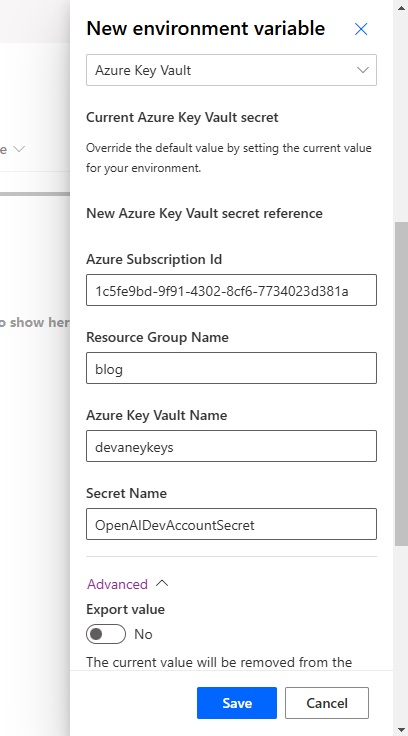
Add a current Azure Key Vault secret and fill-in these details:
- Azure Subscription Id
- Resource Group Name
- Azure Key Vault Name
- Secret Name
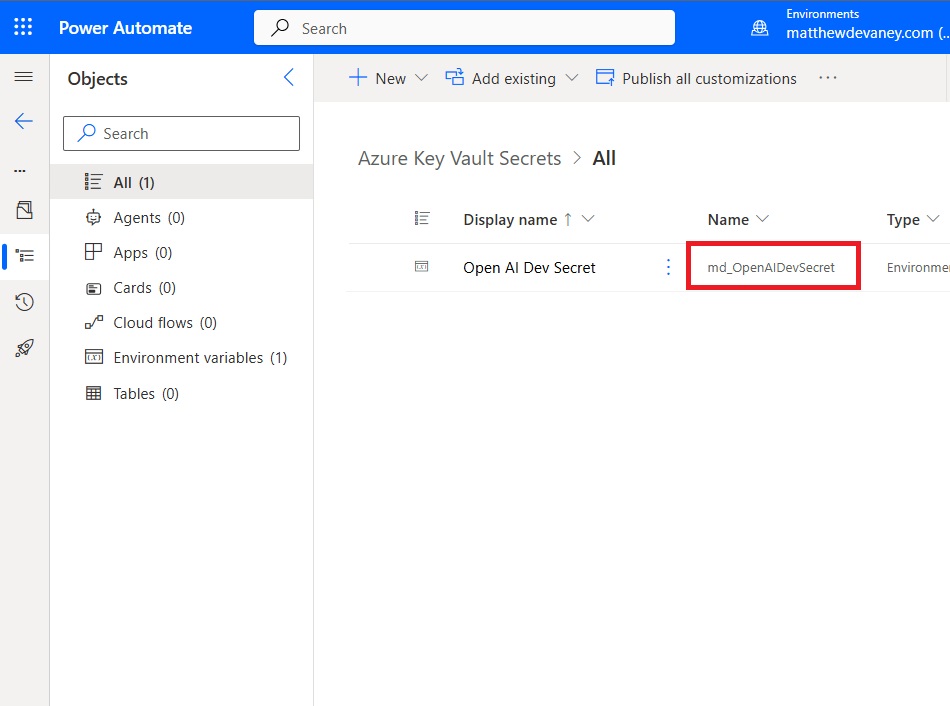
Save the Power Platform environment variable secret. Make a note of the secret name for use in the Power Automate flow.
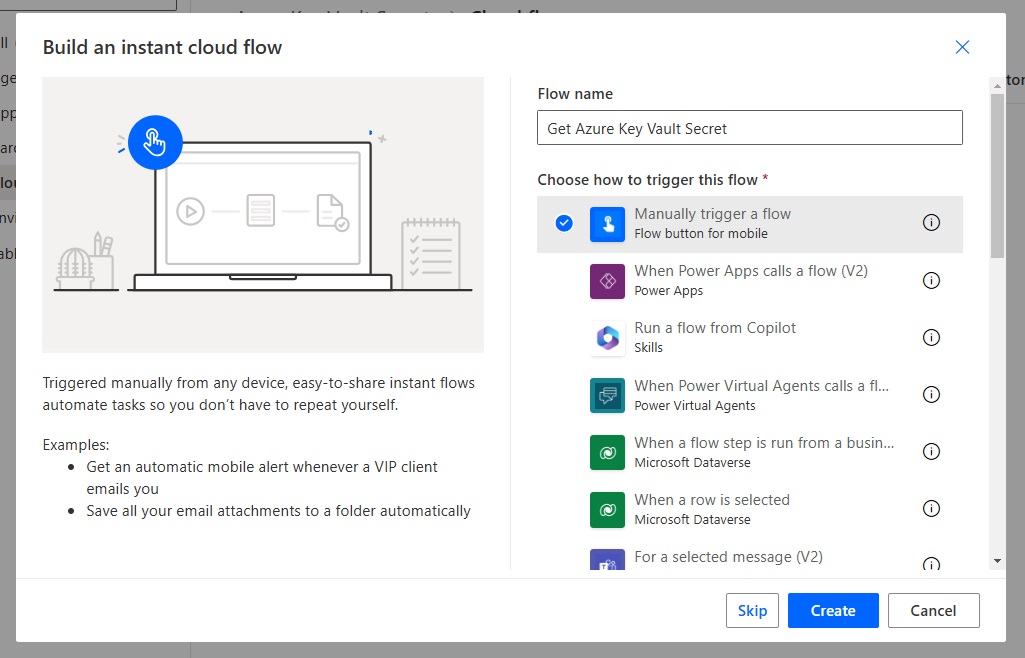
Perform An Unbound Action To Retrieve A Secret Value
We want to build a Power Automate flow to get the secret from Azure Key Vault using a Power Platform environment variable. Open Power Automate and create a new instant flow named Get Azure Key Vault Secret.
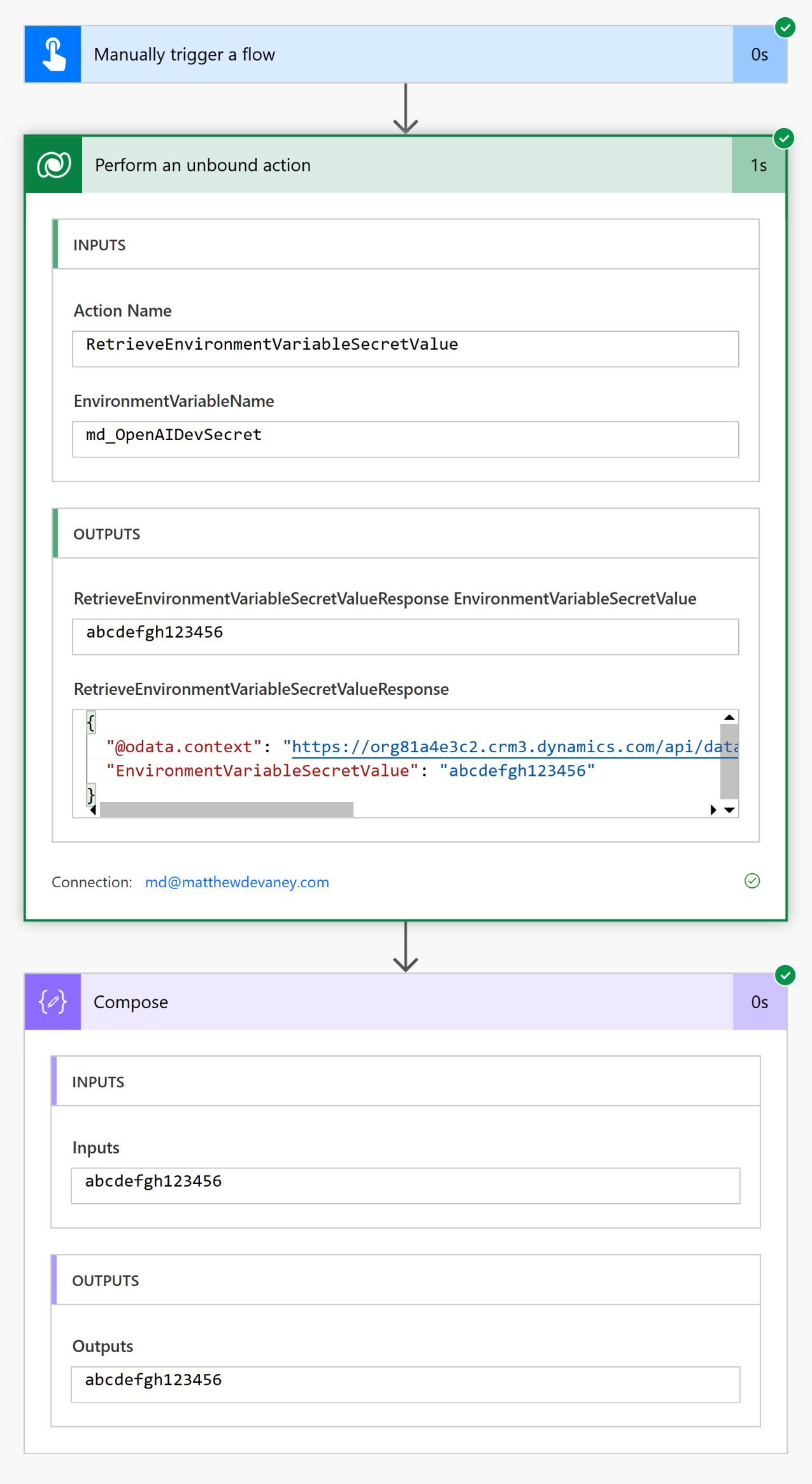
Add a Dataverse – Perform An Unbound Action action after the flow trigger. Select the action named RetrieveEnvironmentVariableSecretValue. Supply the logical name of the environment variable to the flow action. Then insert a Compose action and input the Environment Variable Secret Value from the unbound action for testing purposes.
Save and run the flow to watch it in action. The unbound action fetches the secret value from Azure Key Vault and the result appears in the Compose action.
Secure Inputs & Outputs To Hide The Secret Value
A secret value should not be exposed to any user of the flow. If a user knows how to use a secret value they could potentially use a service the company is paying for unauthorized purposes. To prevent this we can hide the secret value in the flow run history.
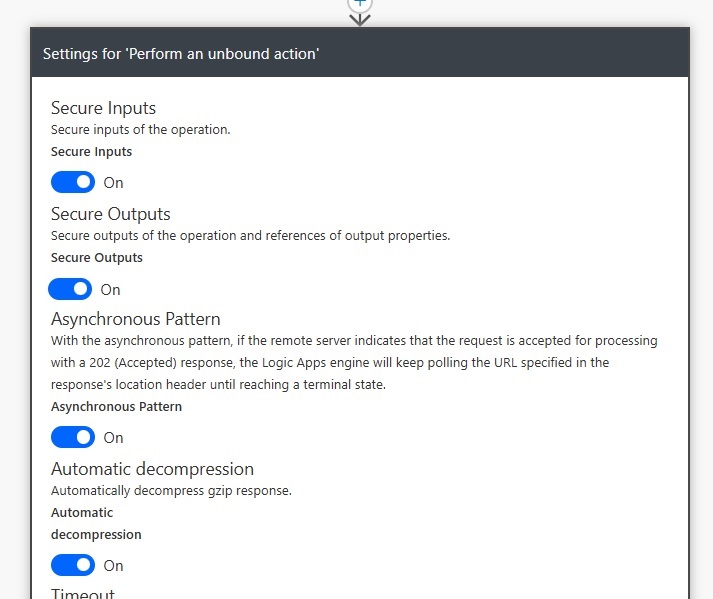
Go to the flow action named Perform an unbound action and open the Settings menu. Toggle on both Secure Inputs and Secure Outputs settings then press Done.
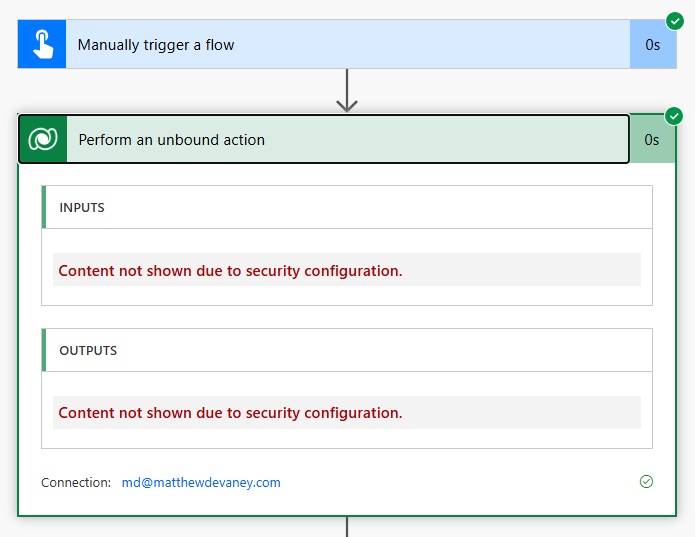
The flow run history will now display the words “Content not shown due to security configuration” on all subsequent flow runs. Prior flow runs will still expose the secret value.
Did You Enjoy This Article? 😺
Subscribe to get new Power Apps & Power Automate articles sent to your inbox each week for FREE
Questions?
If you have any questions or feedback about How To Setup Power Platform Environment Variable Secrets please leave a message in the comments section below. You can post using your email address and are not required to create an account to join the discussion.





